*
Merger and acquisition teams typically range in size from a handful of members in smaller or medium-sized organizations to several hundred internal contributors at enterprise scale. That’s on the buyer’s side as well as on the seller’s teams and includes investment banks or Private Equity (PE) firms.
This headcount, however, doesn’t yet include external contributors. Think research analysts, M&A advisories, outside legal counsel, data protection and privacy compliance consultants, and IT integration specialists. Most of them are involved at one stage or another of the M&A process.
Since the beginning of the COVID-19 pandemic, many internal and external M&A team members have accessed sensitive documents from their home offices. On tight deadlines, they collect, create, review, edit, and share sensitive data that can make or break a deal – or kill it, if that data falls into the wrong hands.
M&A activities at an all-time high – and deal leaks, too
The shift to remote and hybrid work is a powerful driver behind banks and their corporate clients leveraging enterprise-level Digital Rights Management (DRM) to secure M&A-relevant unstructured data. The reasons quickly become clear when we look at a real-life example.
A global automotive component manufacturer is planning with its investment bank the acquisition of a publicly traded semiconductor design and manufacturing company.
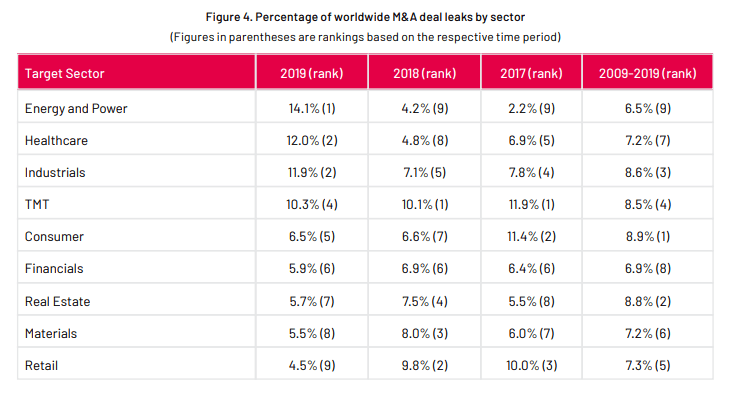
Source: SS&C Intralinks 2020 M&A Leaks Report[PDF]
It’s high season for M&As, and the planned deal seems like a match made in heaven. Yet from an M&A security perspective, the timing couldn’t be worse. M&A leaks have been spiking recently, according to the SS&C Intralinks 2020 M&A Leaks Report [PDF]. This development means all new M&As face an unprecedented challenge.
The challenge: Remote work amplifies M&A security risks
We’ve highlighted document security risks for banks and financial firms resulting from remote work before. The threat level is even more elevated for members of the extended M&A team who work from home. Preparation and execution of most mergers and acquisitions involve a wide variety of confidential documents – in some cases, thousands of them.
Niche vendors of M&A tool platforms tout the cloud-based Virtual Data Room (VDR) as the solution. Such “deal rooms” have become a fixture in the M&A space. At the same time, data protection experts say that VDRs instill a false sense of security – comparable, perhaps, to standard M&A non-disclosure agreements.
These critics point to the weak – often password-based – security of VDRs and specialized M&A document management systems that can too easily be circumvented. Deal administrators and IT lament interoperability issues with other cloud storage services, as well as manageability and scalability problems.
The solution: data-centric M&A security
Enterprise DRM enables IT to strengthen M&A security instead. Fasoo Enterprise DRM, for example, enables data owners to protect confidential content through all stages of a merger or acquisition.
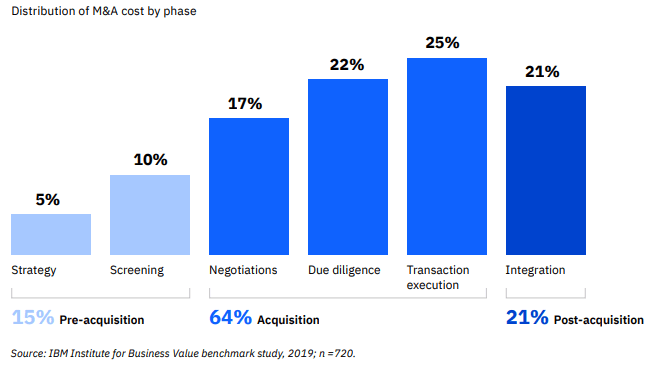
Source: IBM Benchmark Insights: Assessing Cyber Risk in M&A
In our example, we focus on negotiations, due diligence, transaction execution, and implementation. These are the M&A stages where data breaches and deal leaks can be most damaging and costly.
Let’s take a closer look at how the acquirer, its bank, and the acquisition target leverage EDRM to maximize document protection. Enterprise DRM’s data-centric security enables IT and deal administrators to protect, control, and track sensitive data on a per-document basis, on any device, at any time.
M&A and beyond: document lifecycle protection
Fasoo encrypts confidential files at the point of creation or before they get uploaded to a VDR, for example. This protection applies throughout the entire document lifecycle, regardless of which M&A platform any contributing organization may be using.
- Negotiations: Centralized policy management enables M&A data owners and deal administrators to remain in control. Fasoo Enterprise DRM lets them flexibly adjust who can access, edit, print, or share sensitive content – including remote workers.
This phase usually involves a high amount of various Microsoft Office document formats and Adobe PDF files. Dynamic permission control enables deal administrators to assign and revoke file access permissions for reviewers on a temporary basis, for example, to facilitate more than one bidding round.
- Due diligence: In our example, the due diligence document list includes (among others) intellectual property (IP) files, tax records, financial planning P&L documents, electronic design automation (EDA) diagrams, facility blueprints, tax filings, HR records, and all sorts of legal PDFs.Throughout the document review process and beyond, data owners and deal administrators centrally manage who has access to sensitive content. Context-aware and hardware-agnostic secure print and pull print capabilities prevent the unauthorized printing of Personal Identifiable Information (PII) at a home office printer or in a shared workspace, for example. Secure screen and watermarking features (“Fasoo Smart Screen”) block or deter screen capture attempts across all applications, including in Virtual Desktop Infrastructure (VDI) environments and browsers.
- Post-transaction / implementation: M&A security professionals warn that the post-merger integration of the acquired company with the buy-side is fraught with data protection and compliance risks that can cost the acquirer millions or even billions of dollars. Data breaches are one main reason for the high M&A failure rate.In our example, the acquirer already has Enterprise DRM in place across its global organization, not unlike this Fasoo customer in the same industry. This means trade secrets, personnel PII, even sensitive records exported from databases are automatically detected, classified, prioritized and encrypted when they enter the buyer company’s environment from the acquired company.
During each M&A stage and long thereafter, Enterprise DRM provides persistent protection and consistent tracking. A document usage audit trail keeps IT, compliance managers, and financial regulators in the loop.
After all, “digital M&A became the new norm” during the pandemic, according to the consultants at Bain & Company. This year, more dealmakers discovered the power of Enterprise DRM. They use it to prevent M&A leaks and data breaches from becoming a new norm, too.