*
How well is your print infrastructure protected against security breaches? When market research firm Quocirca posed this question to more than 500 IT leaders worldwide at the end of last year, their response wasn’t exactly reassuring.
Only 33 % of respondents in the U.S. said they were completely confident, a drop from 50 % before the COVID-19 pandemic. What happened?

Source: Quocirca Infographic
Work-from-home (WFH) arrangements are to blame, says Quocirca. And you thought unmanaged home office computers already created enough of a headache for IT? Well, think again.
The Quocirca report shines a harsh light on a piece of office equipment that’s omnipresent but often overlooked as a risk factor: the printer.
Increased risk through WFH printers
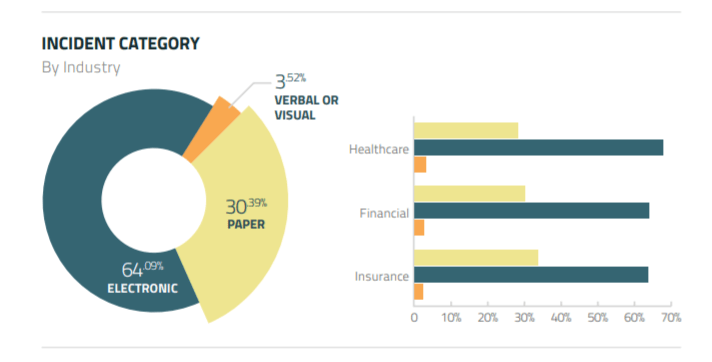
Printers remain underestimated as a threat to document security, and not for lack of evidence: 30 % of data breaches last year involved paper documents, according to the 2021 Privacy Incident Benchmark Report published by incident response specialist RadarFirst.
That’s 13 % down from the year before. But don’t pop open the champagne just yet. This number doesn’t account for sensitive data, such as Personally Identifiable Information (PII) of customers, that was mishandled or intentionally exfiltrated via unmanaged and unmonitored WFH printers. After all, who’d be able to tell?
Source: RadarFirst Infographic
Let’s put the risk in perspective. It’s helpful to remember that modern printers and print/scan/photocopy/fax multifunction devices are special-purpose computers. As such, they are susceptible to software exploits, online attacks, as well as data theft and leakage by insiders. But unintentional or deliberate misuse of printers and printouts aren’t the only risks to consider.
Auditability and chain-of-custody requirements are of equal concern. For example, in financial services, healthcare, and pharmaceutical companies, regulatory compliance demands the traceability of the PII paper trail. In the criminal justice system, another example, the law requires tracking the movement of evidence through its collection, safeguarding, and analysis lifecycle. This includes documenting when files are printed, by whom, and for what purpose.
I’ve written about printers and their role in data theft and leaks on this blog before here, here, and here. If mortgage applications or medical record printouts, for example, are left unattended in the paper output tray and end up in the wrong hands, the result may be costly. Think brand damages, litigation, or steep penalties and other enforcement action by state and federal regulators.
Do we need monitored print stations for remote workers?
Many organizations mitigate such risks to a certain degree by setting up dedicated print stations with closely monitored secure printers. Print activities of remote workers and how they handle the printouts, on the other hand, remain out of sight and beyond the control of staff. So what are IT’s options then?
Too often, these options are limited by a lack of resources – or outright impractical. Support employee-owned printers? Talk about a rabbit hole. Provision company-owned printers to remote workers and block unmanaged devices? Prevent employees from printing at home altogether?
Wanted: a sensible yet effective method to prevent confidential data from seeping out of some inkjet printer in a home office nook, without invading the privacy of remote employees. Enter secure print.
What is “secure print”?
The term “secure print” (or “secure printing”) describes functionalities that enable the prevention and detection of document leaks or exfiltration via print output. In digital rights management at the enterprise level (Enterprise DRM or EDRM), policy-based print protection enables data owners to centrally set and manage print-at-home rules, as well as mark unauthorized printouts.
Fasoo Enterprise DRM takes a printer-agnostic approach to secure printing. This eliminates problems with using different printers or print drivers. Here’s how it works:
The basic print permission setting is part of the Fasoo-encrypted document. In addition, Fasoo’s secure printing component – a.k.a. Fasoo Smart Print – lets organizations apply print protection policies on various levels, for plain and EDRM-secured documents alike.
Fasoo print protection enables organizations to
- prevent printing of files that contain PII or other sensitive information, based on predefined patterns in the document, or mask sensitive data; users can request an exception to print an unmasked version;
- require authentication before retrieving a printout, and also require users to enter a PIN or use a smart card before releasing a print job for added security;
- apply visible watermarks that show a user name, date, time, IP address, and other company information to printouts without user intervention, to deter insider theft and as future forensic evidence; users can request an exception to print without a watermark.
Smart Print’s file-centric print protection means that IT maintains control and oversight regardless of which physical or virtual printer is used. A granular audit trail, including the text or image of the actual printed content, ensures maximum visibility into all print activities by employees and vendors.
For maximum print security in a WFH world, deploy Fasoo Smart Print as your organization’s remote network of monitored print stations – without the creepiness factor.
Find out more about secure printing with Smart Print and Fasoo Enterprise DRM here.
###