Unstructured Data
Control the Unstructured, Secure Your Data
Is My Unstructured Data Protected?
Over 80% of corporate data resides in documents across file shares, cloud repositories, and endpoints. This data is often unorganized, redundant, and highly vulnerable to theft and loss. Do you know where your sensitive documents are and who has access to them?
The average cost of a data breach reached $4.88 million as of 2024.
Source: IBM
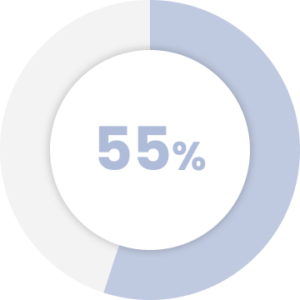
of an organization’s data is “dark,” and the bulk of that dark data is unstructured.
Source: Splunk and TRUE Global Intelligence

Since the pandemic began, the FBI has reported a 300% increase in reported cybercrimes.
Source: IMC Grupo
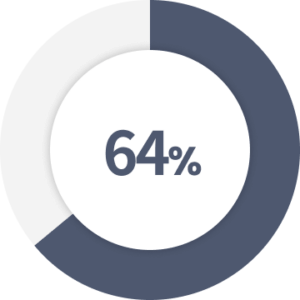
of Americans have never checked to see if they were affected by a data breach.
Source: Varonis
Traditional data protection solutions often lack a comprehensive, lifecycle approach to managing unstructured data.
Limited visibility into where sensitive documents are located
Identify and locate sensitive documents across repositories, cloud platforms, and endpoints.
Focus security and compliance efforts only on high-risk documents, improving efficiency and reducing unnecessary overhead.
Need to apply controls for protection and compliance
Classify documents to assign appropriate security and compliance measures.
Protection and compliance controls are consistently applied, enforced and dynamically updated as needed.
Security and compliance gaps exist when data is shared.
Encrypt and apply granular rights to proactively safeguard documents during sharing.
Advanced protection methods ensure security and compliance for work-from-home (WFH) and third-party sharing scenarios.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with a Data Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Intergovernmental Organization Safeguards Highly Classified Data

What Unstructured Data is Sensitive?

Top 10 Tips To Prevent A Data Breach

Webinar: Overcoming Unstructured Data Security

Whitepaper: Fasoo Data Security Framework


