Challenges
Up in the Clouds
Your sensitive data may be encrypted when stored in the cloud, but what happens when users download and use it?
What if it gets into the wrong hands?
You lose all control and visibility.
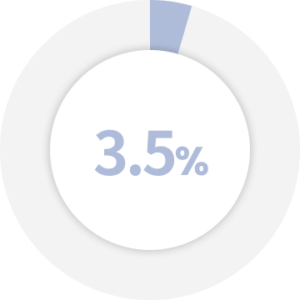
Cloud account compromises cost about 3.5% of organizational revenue in a 12-month period.
Source: cybertalk.org
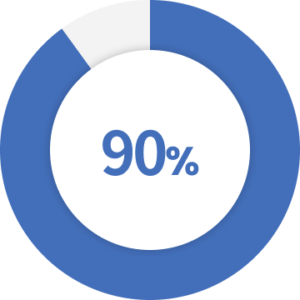
of data breaches target external cloud assets (servers).
Source: Verizon’s 2021 DBIR
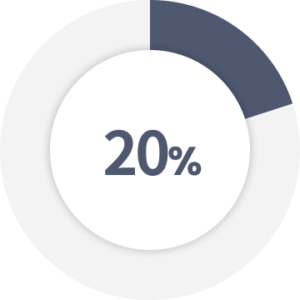
In 2020, “only” 20% of organizations experienced cloud security incidents.
Source: cybertalk.org
Organizations lack visibility and control over sensitive documents stored,
accessed and downloaded across hybrid and multi-cloud environments.
Access to sensitive documents is
improperly configured and
inconsistently implemented.
Bind identity policies
to the document.
Consistent identity and access
policies stay with the document.
Documents emailed
or downloaded lose
cloud-imposed controls.
Apply enterprise
security policies centrally to
all sensitive documents.
All sensitive documents
maintain enterprise controls
regardless of location.
Compliance is difficult to
control and audit.
Automatically classify, tag and
trace sensitive documents as
they are created.
Embedded controls and trackers
enforce regulations and provide an
auditable document trail.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Resources

6 Vulnerable Points In Your Data Security Architecture and How You Can Protect Them

Fasoo Enterprise DRM

The Cloud Is A File Cabinet – Make Sure You Lock It

Are You Crazy To Store Data In The Cloud?

Cloud Computing Is Not Just For Big Companies


