Elevate Source Code Security
to the Next Level
Protect Your Source Code
Source Code Security: Needed, but How?
CISOs and CIOs acknowledge the significance of source code security, but achieving robust protection is challenging. Conventional access control, perimeter-based security solutions and network isolation approaches may be effective against external cyber-attacks but fall short in preventing code leaks and addressing malicious insider threats. The complexity of development environments, with a diverse range of source code platforms and applications, compounds the challenge of building comprehensive source code security.
Complete Your Source Code Security with Fasoo EDRM
It is crucial to adopt a data-centric security model that prioritizes the protection of the source code itself:
to effectively address security risks.
By implementing this model, you can protect your source code persistently from external cyberattacks
and insider threats during its whole lifecycle.
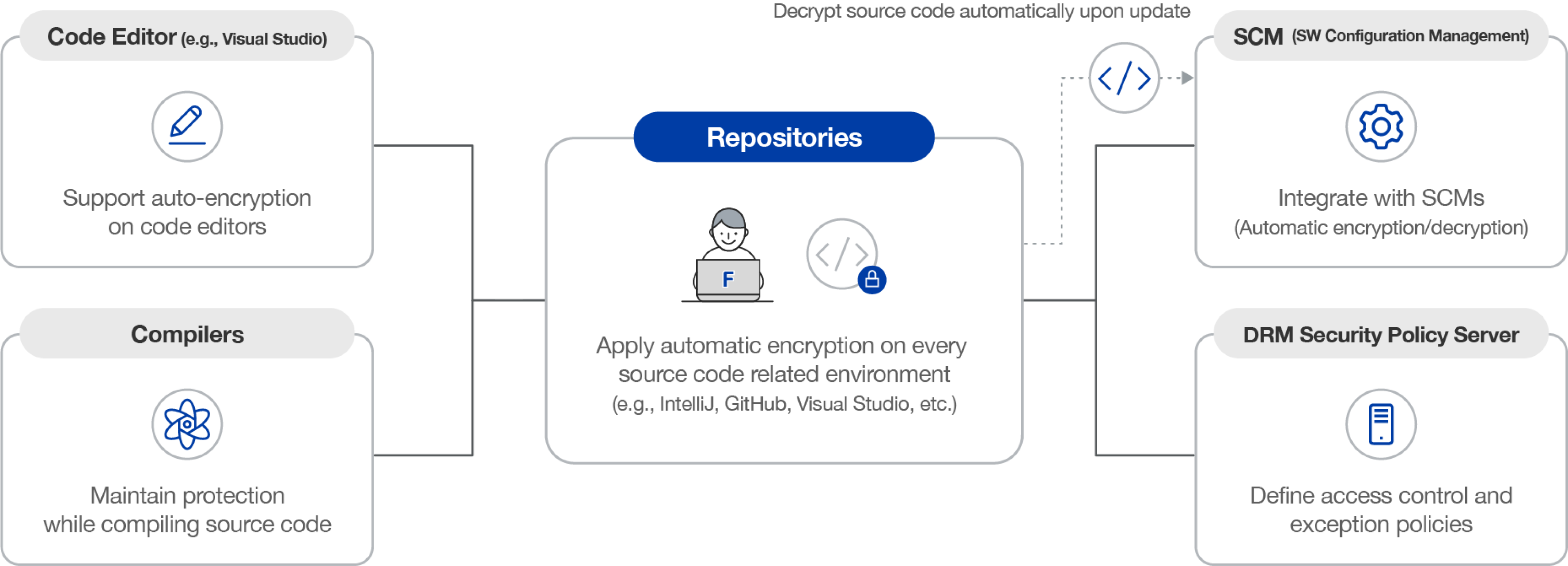
Key Features of Fasoo EDRM for Source Code Security
Automatic Encryption
Automatically encrypts all source code, regardless of the development language or work environment, ensuring comprehensive protection.
Granular Access Control
Grants different access privileges to individuals or groups, enabling organizations to implement granular control.
Comprehensive Audit Trail
Provides detailed usage information for encrypted source code, allowing you to track and identify any unauthorized access or usage.
SCM Integration
Integrates seamlessly with configuration management solutions, striking a balance between security and productivity.
Fasoo Enterprise DRM
Book a Demo

Fasoo Enterprise DRM
Explore more about
Fasoo Enterprise DRM

Resources

Fasoo Enterprise DRM – Product Overview
Videos
Watch how Fasoo Enterprise DRM empowers zero-trust security by protecting, controlling, and tracking your data with its file-centric security.

Source Code Security Brochure
Brochures
Optimal source code security requires seamless integration with coding programs, applications, and software configuration management systems.

How does Fasoo Enterprise DRM (EDRM) compare to Microsoft Purview Information Protection?
Blog
The first solution is an enterprise digital rights management platform to protect documents at scale in large organizations and along their supply chain.
Want to see Source Code Security in Action?
Enter your information to speak with a Fasoo representative about how to complete your source code security with Fasoo Enterprise DRM

