Fasoo’s Approach to Zero Trust Data Security Platform
Zero Trust is not a product.
It’s a model.
Vendors’ approaches to Zero Trust Data Security vary significantly and most fall short of the higher standards Zero Trust demands.
Learn more about Zero Trust Data Security Platform (DSP)
The Ultimate Micro Perimeter
Fasoo takes a different approach than today’s traditional solutions. We push controls and security to what needs protection – the file – and bind them so safeguards travel everywhere with the file.
Sensitive data is always protected, visibility is never lost, and policies are persistent.
Access Privileges
Identity aware access,control by user, roles and groups
Embedded ID
Track and manage files anywhere,know access usage, remote delete
Granular Rights
Restrict what users cando with the document
Encrypt
Data itself is persistently protectedand travels with file
Download Zero Trust Data Security Platform (DSP) Brochure Now
Scale to Address the Hybrid Workplace
Fasoo’s approach inherently scales to the hybrid workplace with files
that self-protect and control themselves everywhere.

Stronger Protection Enforced
DLP and behavior analytics query, observe, allow/block, and assess files to make sure you follow rules or check for anomalous events, but don’t usually protect the data itself. Exposed data is exfiltrated and goes undetected for weeks, if not months. Encrypt sensitive files without exception from the start. It’s what Zero Trust means by explicit, not implicit trust.
Automatically discover, classify, and persistently encrypt sensitive files when they are created or modified.
Discover
Classify

Encrypt
Get Data In Use Under Control
What happens today with traditional solutions after an insider gains access to a sensitive file? It’s a free pass. Copy, cut, paste, share, and store sensitive corporate data as they wish. That’s not Zero Trust. Why let a user extract or share data when all they need is to view and read the document? That’s not the least privilege access.
Fasoo enables explicit granular rights, so users have what they need to do their job but no more.
Continuous Monitoring
Zero Trust depends on continuous monitoring. Who accessed the data, what was done with the data, and from what location and device. But today’s solutions lose sight of data and the interactions as they move across a patchwork of siloed security and IT tools. Context is lost, and Zero Trust is compromised.
Fasoo’s embedded file ID makes tracking and monitoring easy with files that self-report all
interactions to a single lifetime log that makes continuous monitoring easy.
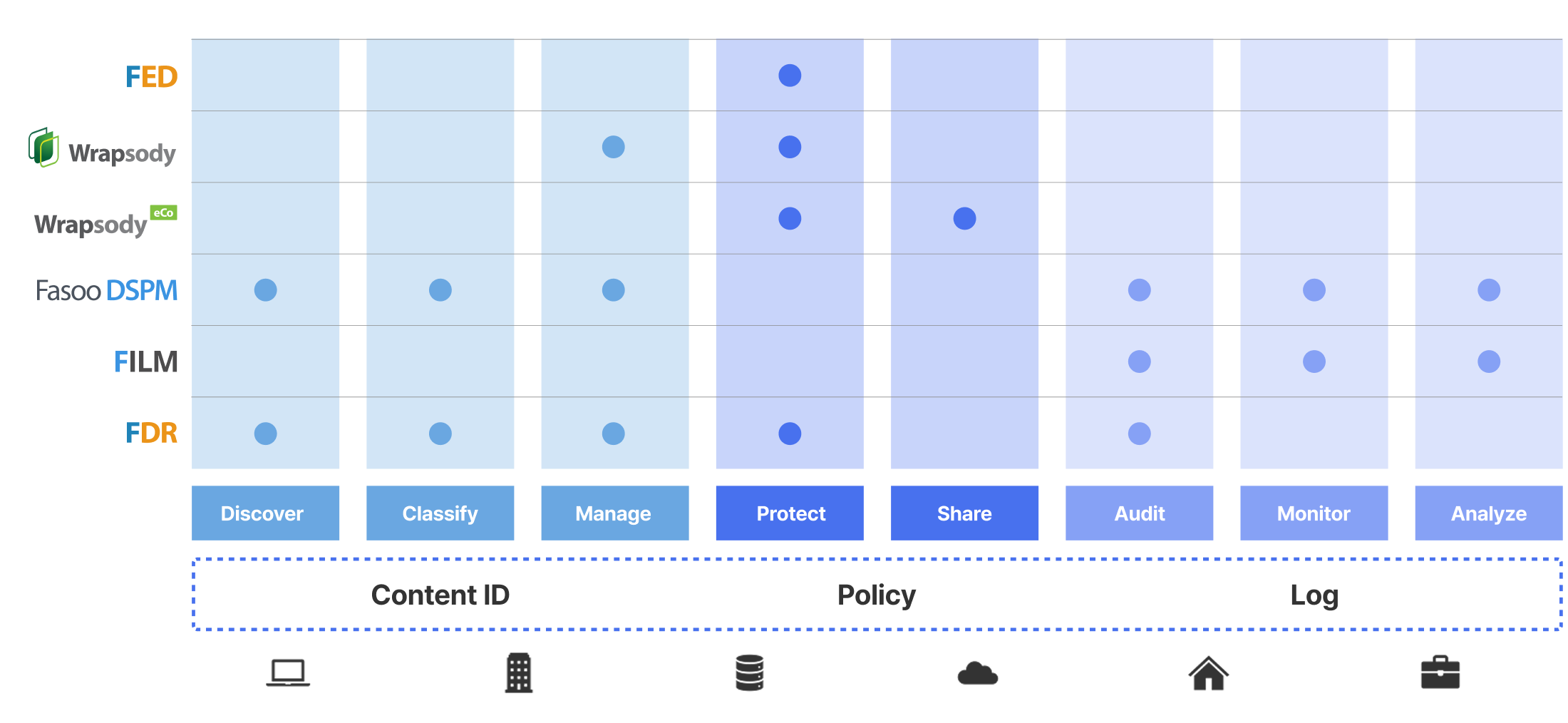
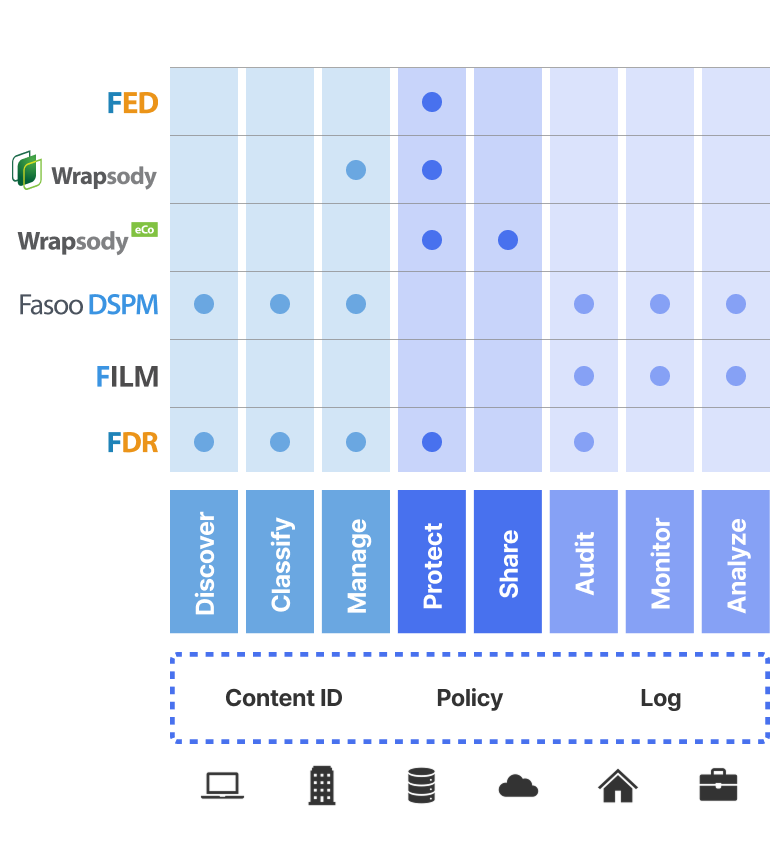
Advanced Data Security Platform
Organizations on the Zero Trust journey leverage their existing data security infrastructure with Fasoo’s Zero Trust Data Security Platform and modular product solutions. We enable security teams to target immediate need use cases with a breadth of solutions that range from the full lifecycle of sensitive data security to regulatory requirements.
Fasoo Enterprise DRM
Meet with a Zero Trust Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Why do you need a Zero Trust Data Security Platform?
Blog
Zero Trust is a major trend in 2022 and one that affects public and private sector organizations alike. Last year when the Biden administration in the US issued its Executive Order on Improving...

Build a True Zero Trust Data Security Platform
Presentation
This new presentation shows how using a true zero trust Data Security Platform simplifies and eliminates organizational complexity, by focusing on universal control of your sensitive data wherever it goes.

Three Essential Capabilities to Bring DLP up to Zero Trust Standards
Blog
DLP does not control how you use a file once a user opens it. Adding encryption, data-in-use protection and continuous monitoring to make dynamic, explicit decisions each time a user accesses sensitive files enhances DLP to protect the data itself.
What is it?
Data classification is the process of organizing and categorizing data based on its level of sensitivity, importance, and confidentiality. This helps organizations manage their data more effectively by ensuring that sensitive information is protected and accessed only by authorized personnel. Data classification typically involves assigning labels or tags to data based on predetermined criteria, such as the type of data, the level of sensitivity, and the potential impact of unauthorized access or disclosure. Data classification can help organizations comply with regulations and legal requirements related to data privacy and security, as well as protect against data breaches and cyber-attacks. It can also help organizations optimize their data storage and management strategies by identifying which data is most valuable and should be prioritized for backup, retention, and archival purposes.
Data protection refers to the set of measures and practices designed to safeguard data from unauthorized access, use, disclosure, or destruction. This includes protecting data from various threats, such as cyber-attacks, data breaches, accidental deletion or corruption, and physical disasters. Data protection typically involves implementing security controls and protocols, such as access controls, encryption, firewalls, intrusion detection and prevention systems, and backup and recovery procedures. It also involves ensuring that individuals and organizations handling data are trained and aware of their responsibilities to protect data and comply with data protection laws and regulations. Data protection is important for maintaining the confidentiality, integrity, and availability of data, as well as building trust with stakeholders who rely on the organization to protect their sensitive information. It is also becoming increasingly important as data privacy laws and regulations continue to evolve and place greater emphasis on data protection and accountability.
Data visibility refers to the ability to access, view, and understand data. It is the process of making data accessible and usable to individuals and organizations for analysis and decision-making purposes. Data visibility can be achieved through various means, such as data visualization tools, reporting software, and data management systems. Data visibility is important for effective decision-making and analysis, as it allows individuals and organizations to make informed decisions based on accurate and up-to-date information. By improving data visibility, organizations can gain a better understanding of their operations, customers, and markets, and make more informed decisions to achieve their goals. Data visibility can also help organizations identify areas for improvement and optimize their business processes. For example, by analyzing data on customer behavior and preferences, organizations can identify trends and patterns that can inform product development and marketing strategies. Overall, data visibility plays a critical role in helping organizations achieve their strategic objectives and stay competitive in their industries.

