Enterprise Digital Rights Management (EDRM)
Threats have evolved and so must control and protection of sensitive data. Fasoo delivers capabilities that meet today’s challenges and architectures.
Download Fasoo Enterprise DRM White Paper Now
A Refresh in the Age of the Hybrid Workplace and Zero Trust
Gartner reports EDRM deployments are on the rise as traditional data loss prevention solutions fail to scale and Zero Trust sets a higher bar to control and protect sensitive data. Learn what’s driving EDRM’s resurgence.
Persistent Protection and Control
EDRM is different from DLP, CASB, and EPP technologies that sit at data ingress/egress points and mostly observe, rather than protect, the data. EDRM places controls and maintains persistent encryption closest to what needs protection – the file – and bind them so safeguards travel everywhere with the file.
Sensitive data is always protected, visibility is never lost, and policies are persistent.
Access Privileges
Identity aware access controlby users, roles and groups
Embedded ID
Trace files anywhere, know accessusage, remote delete
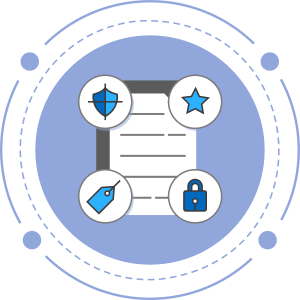
Granular Rights
Restrict what users cando with the document
Encrypt
Data itself is protectedand travels with the file
the Enterprise DRM
market since 2000”

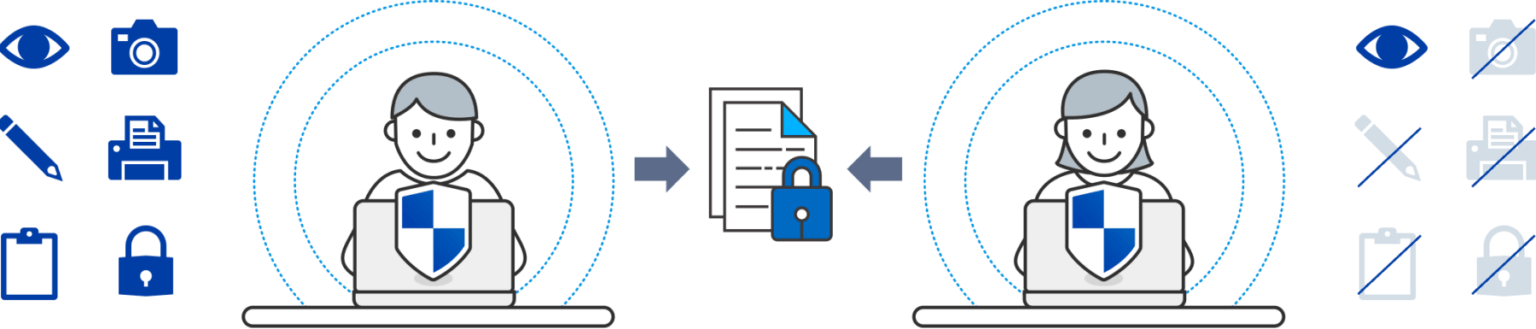
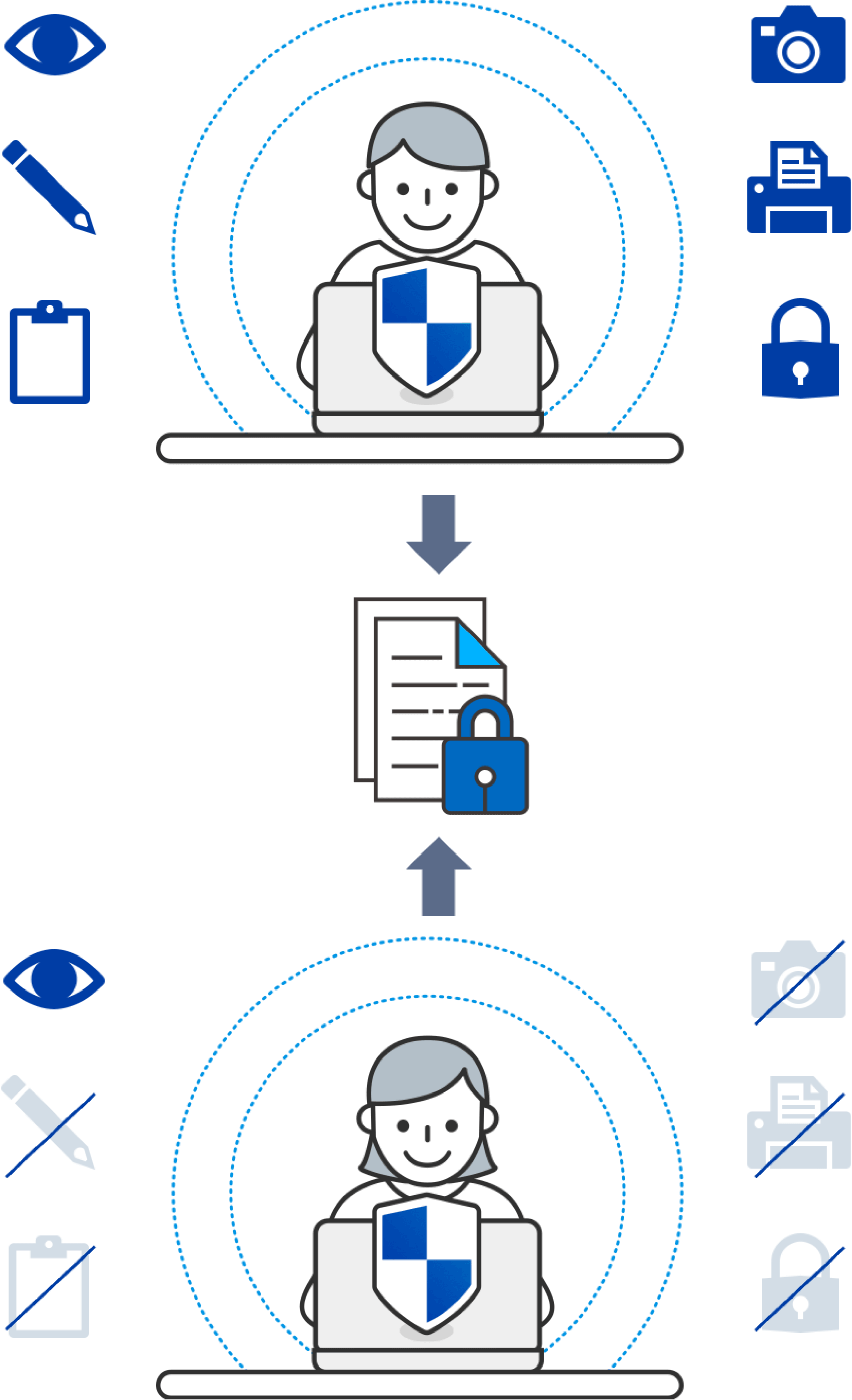
Data In Use Controls Stop Insider Threats
What happens today with traditional solutions after an insider gains access to a file? It’s a free pass to copy, cut, paste, share, and store sensitive corporate data as they wish. EDRM lets organizations take control with granular rights that limit how an insider uses your sensitive data. And with efficient security management, exception policies can be put into place when an admin is unavailable.
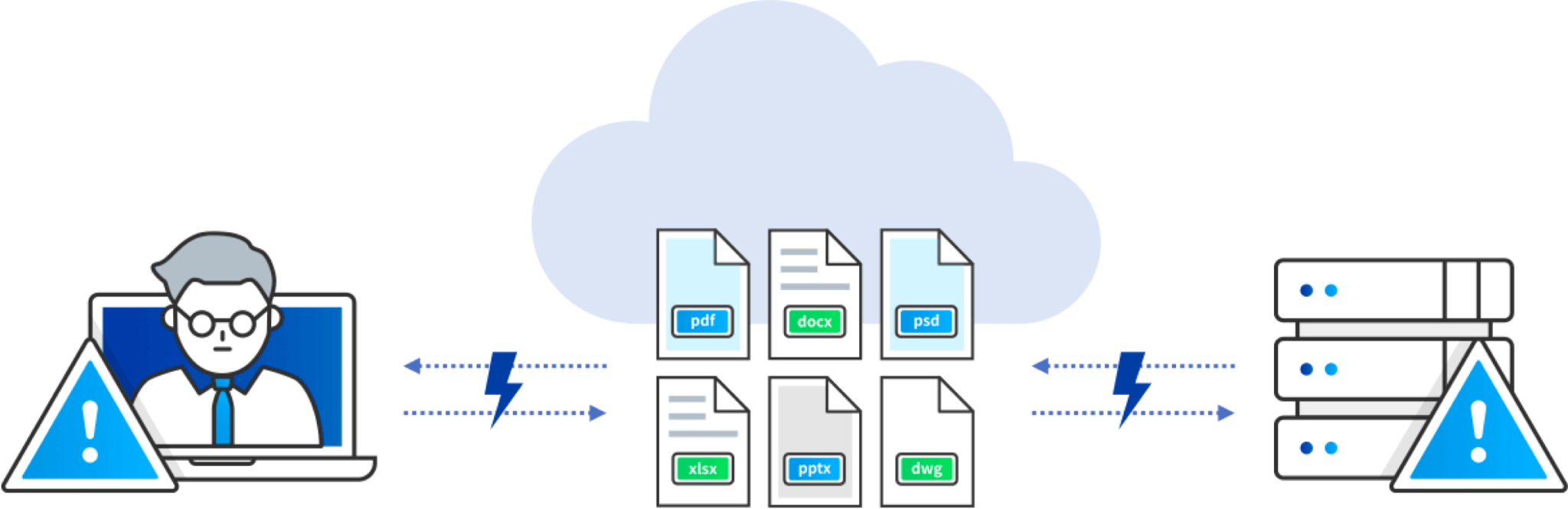
Eliminate Cloud Misconfiguration Risk
Gartner projects that “through 2025, more than 99% of cloud breaches will have a root cause of preventable misconfigurations or mistakes by end-users.” EDRM centralized policies and location-agnostic safeguards travel with sensitive files, so you always have consistent configuration control.
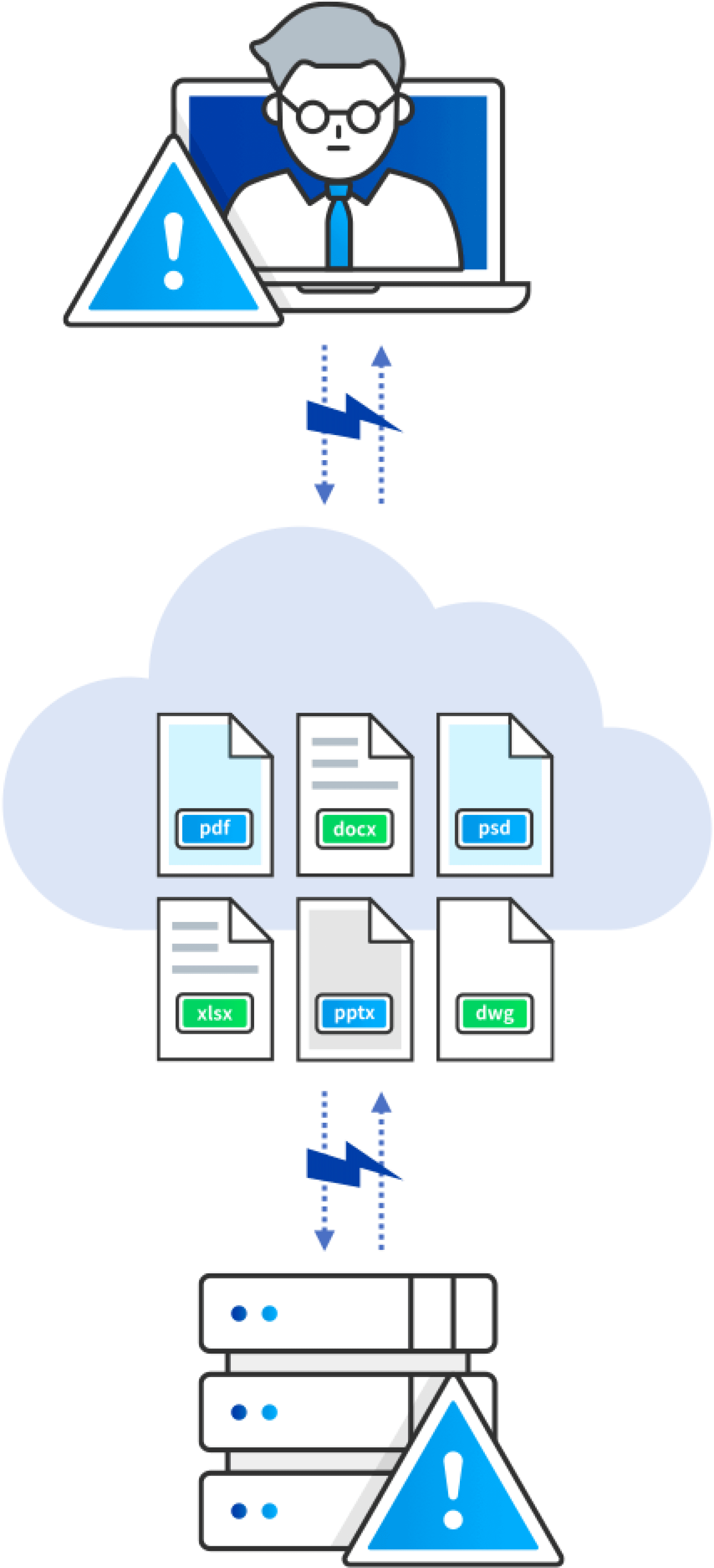
Tracking for Monitoring and Audit
Zero Trust and regulatory compliance rely on data visibility for continuous monitoring and auditing. Today’s solutions lose visibility as data moves around siloed applications and unmanaged assets. Fasoo’s EDRM embeds a content ID so files self-report context about users, devices, and data interactions to a universal log.
Fasoo’s embedded file ID makes monitoring easy with files that self report all interactions
to a single lifetime log that makes continuous monitoring easy.
Zero Trust Data Security Platform
EDRM is a core component of Fasoo’s Zero Trust Data Security Platform. The Platform consolidates data-centric capabilities covering the lifecycle management of sensitive data and advanced Zero Trust features to deliver stronger security with less complexity.
Data-Centric Process
Discover
Classify
Protect
Adaptive Access
Monitor and Control

Fasoo Enterprise DRM
Meet with a Data Security Specialist

Product
Explore more about
Fasoo Enterprise DRM

Resources

IP Theft in the Automotive
Industry: 10 Tips to Counter the...
Blog
No matter if your company is an automotive OEM, Tier 1-3 supplier, or a small engineering studio that serves component manufacturers across various industries...

How to Maximize M&A Security With Enterprise DRM
Presentation
Mergers and acquisition (M&A) activities pose major document protection challenges for all parties involved. Leaked or stolen data has caused bidding wars, broken deals...

How does Fasoo Enterprise DRM (EDRM) compare to Microsoft Purview Information Protection?
Blog
How does a dedicated solution for securing documents compare to an assemblage of protection components with a focus on Microsoft Office applications and files?
What is it?
Enterprise digital rights management (EDRM) is a technology that enables organizations to protect their sensitive data and intellectual property by controlling and monitoring how information is accessed, used, and distributed across various devices and platforms. EDRM solutions typically involve encrypting sensitive data at rest and in transit, and providing access controls and permission settings to limit who can access and modify the data. EDRM can also include features such as digital watermarking, tracking, and audit trails to monitor and track the use of sensitive data. The goal of EDRM is to provide organizations with a comprehensive and integrated approach to data protection, enabling them to manage their data assets effectively while minimizing the risk of data breaches, insider threats, and other security incidents. EDRM can be particularly useful in industries that handle sensitive or confidential information, such as finance, healthcare, and legal services.





