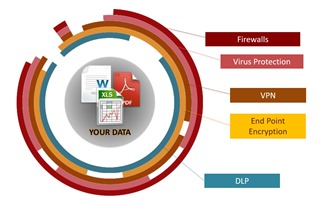
According to the Identity Theft Resource Center (ITRC), just this year to date, there have been 725 reported breaches. The traditional security model to guard the perimeter is not adequate. Today’s challenges require a layered Data Security Framework. So, what should this framework contain to take the right preventative or restorative actions?
For businesses, getting insight and control of their critical files is essential. This includes any new file that is created and saved and any existing files containing sensitive information. Many businesses are significantly challenged with gaining visibility across their environment to understand the location of their sensitive files. They don’t know how many copies or derivatives of a file are floating around on desktops, laptops, file servers, mobile devices, etc. and are not in a position to take appropriate action to secure and control them. Discovery is the first layer to add to a company’s security posture. This helps you find things.
Once the discovery process is completed, now you are ready to protect your sensitive inform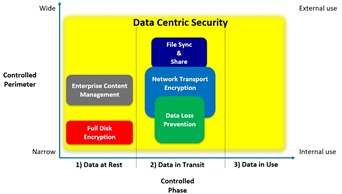
Another layer for an effective data security framework is monitoring activity related to sensitive files. The ability to tie in data from various security technologies, including firewalls, DLP, databases, and even physical security (e.g., entry/exit data from keycard or biometric systems) and employee attendance records can help a business review risky activities and after suitable investigation, help decide whether or not to take action to address them.
A complete framework is required for companies to continuously adjust their security position dynamically to prevent damaging data breaches. Current challenges dictate a good data security framework to take into consideration both human and technological aspects. At a minimum this framework should include regular updating of traditional security measures already in place; educating and training employees; a current data breach response plan and most importantly data-centric persistent security technology measures.

