Wouldn’t it be a shame if it slowed down your business and turned out to be useless for protecting your data? Here’s what I’m getting at:
74 percent of U.S. companies say they will keep some remote work arrangements in place post-pandemic. In other news, roughly 359,000 cybersecurity positions in the U.S. went unfilled at last count.
Taken together, these data points spell trouble. This is where the policy part comes in. Data breaches involving sensitive information have been skyrocketing recently. What about the document access and use policies at the affected organizations? Why didn’t they matter?
You likely know the answer. Remote work, a flood of unmanaged devices, VPN node expansions, and cloud service adoption run wild have created more weak spots than point solutions and understaffed IT teams can handle.
Patch schedules need to be adhered to. Access controls and policies have to be applied and managed. Not to forget the exception requests. Someone has to follow up. But who? And how? “This support ticket will be automatically closed after 5 days.” Will it get resolved before the workflow turns into a work trickle?
It doesn’t help that many point solutions that promise to keep your data secure foster inconsistent policies that leave security and privacy gaps. Your organization could pay a high price if your document protection strategy doesn’t connect the dots and eliminate the gaps and blindspots. Think stolen intellectual property (IP), legal fees, or brand damages.
BYOD report: “Enterprises are running blind”
The point isn’t lost on Anurag Kahol, the Chief Technology Officer (CTO) of cloud security firm Bitglass. Introducing the company’s 2021 BYOD Security Report, he warned in June: “There has never been a more important time for enterprises to seriously rethink their approach and secure all forms of communication amongst users, devices, apps, or web destinations.”
Source: 2021 BYOD Security Report (Bitglass/Cybersecurity Insiders)
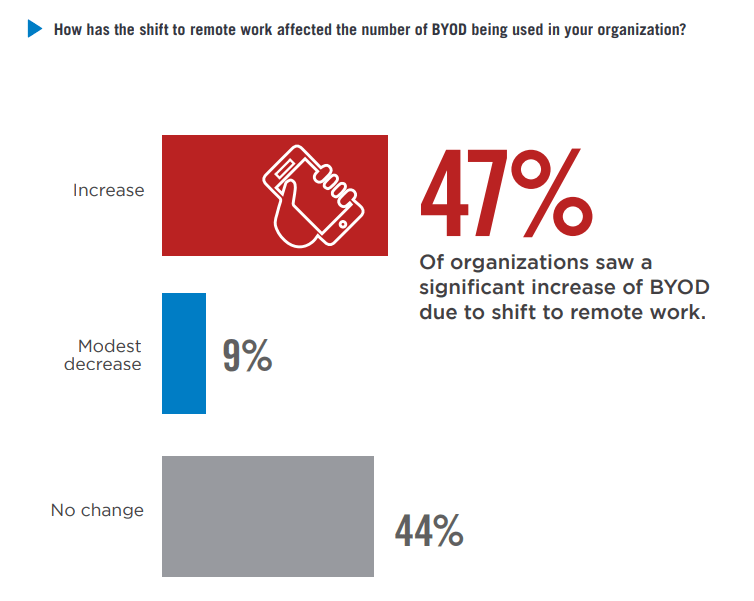
The survey (conducted in collaboration with Cybersecurity Insiders) shows the rapid adoption of unmanaged personal devices connecting to work-related resources (a.k.a. BYOD):
- 47 percent of organizations reported an increase in personal devices being used for work.
- 82 percent said they now actively enable BYOD to some extent.
- The most critical concerns of respondents were data leakage or loss (62 percent), users downloading unsafe apps or content (54 percent), lost or stolen devices (53 percent), and unauthorized access to company data and systems (51 percent).
The survey results also show how ill-equipped companies still are to deal with malware and data theft – more than 18 months into the pandemic. The authors conclude: “Enterprises are running blind.”
Their point is validated by the recent escalation of data leaks following extortion attempts. Yet, while IT teams struggle to stem the tide of malware attacks and data theft, it seems that some large organizations seem better prepared than others in preventing confidential information from leaking or getting stolen. So what’s their secret?
Keep tabs on your data and worry less where it goes
Spoiler alert: There isn’t just one answer, and it doesn’t start with an “A”, as in AI or Automation. Presumed panaceas can do more harm than good if they introduce more complexity instead of minimizing it.
One hint comes from Capgemini and Forrester, who published a joint study on cyber resilience in March. It showed that 71 percent of companies planning to increase their cybersecurity budgets said they now prioritized data-centric security.
Growing investments in enterprise-level digital rights management (DRM) are part of this trend. One example is Fasoo Enterprise DRM. Globally operating businesses and U.S. government agencies rely on Enterprise DRM to secure their unstructured data, such as Microsoft Office documents, PDFs, or CAD designs, at the file level.
Centralized policy management: fewer gaps, faster workflows
Enterprise DRM enables them to automatically encrypt documents at the point of creation. It applies a persistent yet flexible file policy and puts sensitive files under lock and key.
This policy is centrally managed by the organization. What’s the advantage of this approach over, say, the built-in PDF password protection feature already provided by Adobe?
I’ve addressed a few known security deficiencies of the latter method in this post. From the organizational perspective, it means putting the document’s fate into the hands of its creator. The business relinquishes control to individual users. When they leave, the company is forced to dedicate valuable resources to special recovery efforts, or even loses access completely.
In comparison, the main advantage of the centralized policy management provided by Fasoo Enterprise DRM is that the organization always maintains control over its documents and what happens with them, wherever they go. This includes changing policies for a user or group at any time, regardless of where the document resides.
So what about centralized solutions designed to protect a broader range of files across the enterprise? Basic PDF password protection marks one end of the spectrum. On the other end, let’s look at Azure Information Protection (AIP) by Microsoft, for example.
AIP was designed with a focus on protecting documents in the MS Office ecosystem. While AIP lets organizations include a limited range of third-party file formats under its protection umbrella, it also still relies on individual users to make security policy decisions on securing documents. Specific training may be required.
In addition, AIP’s lack of centralized control options makes it difficult to implement and change security policies in organizations with many users and constantly changing roles. The considerable burden of keeping AIP protection up-to-date and in sync with the needs of their department or business unit often falls on the individual creator of the document.
Support requests down, document security up with Enterprise DRM
Team members in a Fasoo Enterprise DRM-protected environment, on the other hand, don’t have to worry that a document may lose its protection or become inaccessible when sent as an email attachment or uploaded to the cloud, for instance.
Each time someone attempts to access a file, this requires a usage license issued by a DRM server. This license is based on parameters such as user, document, device, time, and location. The policy determines who can open a particular file and for what purpose (examples: “view on the screen only”, “view, edit and save “, “print only with watermark”).
The policy applies regardless of which endpoints, storage devices, or cloud services the files traverse. They are protected, and access details are monitored by Fasoo Enterprise DRM, no matter where they wander inside or outside the organization and its supply chain.
What does this mean in case of a data breach? Files secured with Fasoo DRM – example: W-2 PDF forms – are useless in the wrong hands, should they be exfiltrated for wholesale on the dark web.
The same applies to documents with sensitive intellectual property, such as CAD files from the engineering department. If a rogue engineer downloads them to a flash drive to take them to a competitor, like in this case, nothing is lost or compromised.

Safe policy exceptions at startup speed
Why do our customers select Fasoo Enterprise DRM? One main advantage, they say, is its centralized policy management, which puts admins and data owners in control. Policies are implemented platform-agnostic and consistently across the entire data inventory.
Equally important, they stress, is that these policies can be flexibly adjusted at a moment’s notice to support the workflow of global companies running at startup speed.
Customers praise its capability to quickly accommodate changes in security policy to meet changing business needs. Suppose a document owner leaves the organization or changes jobs. In that case, a department manager, IT, or security can easily grant or remove access to the document with the click of a button, regardless of the document’s location.
Another example is the way the exception management approval system handles temporary document permissions. Fasoo Enterprise DRM facilitates a pre-approval, post-approval, or self-approval workflow. Exception approval can be delegated to department heads, managers, or coworkers so that the organization doesn’t have to rely on IT.
Centralized policy management and flexible exception handling are critical for Fasoo customer ZF Group, a global automotive industry supplier. The company deploys Fasoo Enterprise DRM to secure critical IP, such as CAD drawings and process information, in tech centers on three continents.
“You have to find the right balance between maximum IP protection on one side, and productivity on the other,” said Markus Fischer, VP Engineering at ZF Group’s Active Safety Systems. “You need to be able to quickly adjust access privileges on a granular level, without delay.”
###
Find out more about Fasoo Enterprise DRM and its centralized policy management capabilities here.