The eyes of commercial spies, that is.
Intellectual property (IP) theft, most of it on behalf of China, damages the US economy to the tune of about $500 billion a year, says the FBI. Automotive, aerospace, and other innovation-driven tech companies are bearing the brunt of commercial espionage efforts.
What do the nation-states and competitors behind the IP theft have in common? They all rely on a secret weapon: company insiders.
What is an “insider threat”?
The US government’s National Insider Threat Task Force (NITTF) defines an insider as “any person with authorized access to an organization’s resources to include personnel, facilities, information, equipment, networks, or systems.” This not only includes your employees but contractors, partners, and potentially anyone in your supply chain.
In the vehicle manufacturing sector, most sensitive information is now stored and managed digitally: in the form of CAD drawings, for example, or as digital image files, as Microsoft Office documents, or in various Adobe PDF formats, including PDF/A, PDF/E, or PDF/X.
The dependency on these files makes IP theft by company insiders with access to that information the biggest potential security threat for automotive manufacturers and their suppliers today. Under pressure to innovate and develop startup-like cultures, traditional manufacturers struggle to protect their digital IP without sacrificing productivity.
A key security component in this fight is International Cybersecurity Standard ISO/SAE 21434 which specifies engineering requirements for cybersecurity risk management in the design and development of car electronics. It covers cybersecurity governance and structure, secure engineering throughout the life cycle of the vehicle, and post-production security processes. It covers vehicle manufacturers and their entire supply chain. This standard is becoming more important as the industry moves toward autonomous vehicles.
How does someone become an insider risk? What are the warning signs of potential insider theft? Is your company prepared?
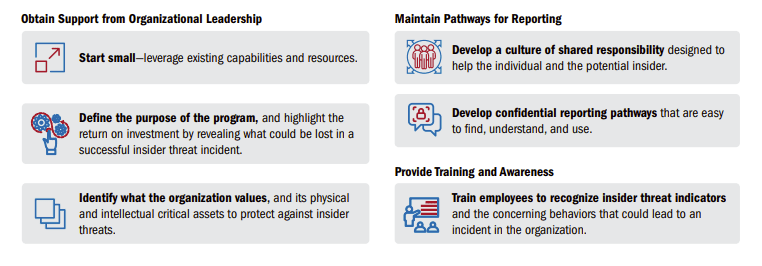
Experts agree: securing unstructured data across the automotive manufacturing supply chain requires a comprehensive approach by Security, IT, HR, Compliance, and Legal. Here’s what they recommend:
1. Raise your organization’s threat awareness.
The battle for the future of mobility is marked by innovation at break-neck speed and tough competition for top performers.
Traditional players find themselves competing with Silicon Valley giants, startups, and nation-state-sponsored groups to recruit and hold on to the best talent. Electric vehicle development, connectivity, battery technology innovation, and the rise of additive manufacturing are changing the industry.
The IP Awareness Assessment, offered by the National Institute of Standards and Technology/Manufacturing Extension Partnership (NIST/MEP), enables affected companies to assess their intellectual property awareness.
Another valuable resource for your internal IP Theft awareness program and training is the National Insider Threat Awareness Month library at the Center for the Development of Security Excellence. It offers guides, real-world case studies, videos, and even web-based games to help organizations detect, deter, and mitigate insider threats.
2. Know the IP theft threatscape.
According to Ponemon Institute research from 2022, 67% of surveyed organizations worldwide reported more than 30 insider-related incidents per year involving digital assets.
In the US and the EU, counterintelligence experts and manufacturing industry security advisers attribute the rise of IP theft mainly to China. Take the Thousand Talents Plan, for example, which was conceived by the Chinese Communist Party.
Officially, TTP is a recruitment program for up-and-coming scientists and engineers to experience China and work side-by-side with their Chinese peers. In reality, it now serves as a vehicle for a state-sponsored IP theft campaign on a global scale, with more than 140 recruitment stations set up in the US alone.
Source: CISA
Social media and business networking platforms (LinkedIn, for example) are increasingly used to identify and target company insiders for later exploitation.
To keep you abreast of recent developments and emerging threats, the FBI provides IP theft prevention resources on its website and sends out email alerts.
3. Identify what’s most at risk of IP theft in your organization.
Unstructured data such as CAD/CAE files, digital images, and confidential sales or legal PDF documents contain your organization’s most valuable intellectual property and blueprints for its future. Yet IT and Security face a unique challenge in protecting it against IP theft.
How to secure these files across the enterprise and along its diverse supply chain? IP protection at the document level often requires that the information rights management service supports all industry-relevant CAD applications.
Automotive engineer
Your teams may currently use mainly one or two such tools. But this can change quickly due to new requirements. Effective information rights management in this dynamic environment makes support for tools such as AutoCAD, CATIA, PTC Creo, Siemens NX-CAD, or SolidWorks essential.
PDF file formats are another example. Does the information protection software cover the broadest possible range of documents? Support for at least 200 file formats is considered the bare minimum in a globally integrated enterprise environment.
4. Determine who’s posing an insider threat.
As paradoxical as it may sound, this question is the easiest to answer. Experts will tell you that any executive and rank-and-file employee, contractor, or temp with access to sensitive information is potentially a risk. This includes external business partners and is made even worse by so many people working remotely or from home.
Security professionals differentiate between malicious, negligent, and compromised insiders. The lines between these categories are blurry. Common scenarios resulting in the loss or theft of proprietary information that involves negligent or compromised insiders:
Negligent insiders
- use passwords like “password” or accidentally send a confidential file to the wrong person,
- (on the IT team) leave Git server content or Amazon AWS S3 cloud storage buckets open for the taking,
- share access credentials with team members.
Insiders are compromised when
- clicking on an email phishing link that downloads a spyware exploit kit,
- inserting USB sticks found in the office parking lot or sent to them by mail,
- working from home on unsecured WiFi on unmanaged compromised devices with remote access to critical company IP.
All of these examples can result in exfiltrated CAD files, office documents, or process information. IT can minimize the risk of unintentional IP exfiltration by controlling access to proprietary information at the file level and limiting or blocking possible ways of sharing, such as copying, printing, or taking screenshots.
5. Prevent the #1 IP theft scenario.
What about the malicious insiders? In the manufacturing sector, who are the real-life spies?
Let’s forget about James Bond and his Minox camera for a moment. Instead, let’s focus on Jill with a smartphone and money problems. Joe in R&D may fancy making VP at a competitor. Then there’s Jim, the work-from-home (WFH) contract engineer who just got an invite to visit China, all expenses paid, courtesy of the Thousand Talents program.
Not to forget the ambitious – now-former – head of your self-driving vehicle division (if you are Google).
That last case reminded us that the risk of IP theft is highest when employees leave. In more than 50% of documented IP theft, the perpetrators are employees who quit and take proprietary information with them.
This happens simply because they could. Nothing got in the way.
A design engineer, for instance, may store critical CAD drawings on a private hard disk or personal cloud storage “just in case” and later use them when interviewing with the competition.
IT and other stakeholders need a mechanism that makes it simple to centrally disable access to sensitive documents for a departing employee at the file level, even if that file now resides on an unmanaged work-from-home laptop.
6. Establish or expand your threat intelligence program.
Managing IP theft risk in 2022 requires more than cursory reference checks or LinkedIn profile once-overs for potential hires.
Smaller companies can outsource their pre-hire background checks to background investigation specialists and threat intelligence firms. Large manufacturers may expand their internal open-source intelligence (OSINT) collection capabilities.
This enables investigators and SOC analysts to examine, for example, dark web marketplaces for suspicious data movements.
Where to find private-sector professionals that specialize in digital insider threats on all levels? Industry associations, trade groups, and government resources such as the National Center for Cybersecurity in Manufacturing can help.
7. Monitor to identify insider threat warning signs.
What are the indicators of insider threats that may culminate in IP theft? Behavioral and personality changes can be early warning signs, experts say. Financial problems, a drop in performance, or a sudden interest in files outside the employee’s work scope are indicators as well.
To catch such telltale signs early on, the software selected to secure and manage proprietary information should include the capability to flag suspicious files and user activities. Do they indicate sufficient risk for intervention by business management?
Digital rights management combined with user and entity behavior analytics (UEBA) enables visibility into employees’ interaction with IP at the file level. It applies rule-based modeling to the respective data sources.
This approach allows the system to establish baseline behavioral patterns and help determine suspicious activities.
Fasoo’s RiskView, for example, provides such UEBA protection for sensitive files. For IT, it serves as an early warning system against infractions by users even with sufficient inside knowledge to bypass other security controls and methods.
8. Choose productivity over paranoia.
Under pressure to innovate and develop startup-like cultures, traditional manufacturers struggle to protect their digital IP without sacrificing productivity.
An overly rigid and inflexible approach to IP protection risks slowing down workflows and alienating top performers.
It also introduces additional risks. A typical example is team members who develop “creative” workarounds to access or share sensitive proprietary information they need to get the job done.
Security or productivity: do we have to choose? It doesn’t have to be an either/or choice. Let’s look at Digital Rights Management (DRM) as an example.
DRM (also referred to as Information Rights Management, IRM) today is at the heart of many enterprise-wide initiatives to prevent intellectual property theft or unintentional digital IP leakage.
How to solve the IP Theft Protection vs. Productivity conundrum? Enterprise IT leaders emphasize the importance of carefully selecting an enterprise DRM software that is flexible and fast at scale.
9. Put manageability and flexibility first.
Can we really expect data owners to become security experts when managing document-level protection for the files they oversee?
We shouldn’t. But that’s what happens, IT says, when the company deploys the kind of information protection service that was developed almost as an afterthought to popular office software and design tools.
Many IT leaders have determined such rights management services are too limited for the use cases in their enterprise-wide deployment. They are also cumbersome to manage and use on the ground.
Exception management is a prime example. How do you give everyone on the team who needs it fast and uncomplicated access to critical IP while ensuring that it doesn’t fall into the wrong hands?
An effective DRM solution simplifies and accelerates the process of obtaining exemptions from file access and management restrictions. A user’s legitimate exception request should not increase IT’s workload, be held up by slow support desk response times, or get forgotten in the system once it has been granted.
10. Select DRM that enables centralized policy and visibility
Opportunity makes thieves, as highlighted in Tip # 5. Eliminate the opportunity for digital IP theft with DRM. Protect your IP from the onboarding through the offboarding process, including all user activities on your network in between.
Centralized policy management empowers IT and management to conveniently set and change data-centric and user-centric document use policies at-a-glance.
The past three years have seen a significant uptick in companies looking to deploy EDRM to prevent IP theft. Industry observers attribute this trend primarily to three factors:
- the rising threat of IP theft by corporate insiders,
- Microsoft now supports its rights management in Azure, on Apple’s iOS, and on Google’s Android,
- the pressure to protect intellectual property accessed by remote workers, often on unmanaged home networks and devices.
Fasoo Enterprise DRM’s authentication APIs, for example, supports numerous 3rd party, federated, and proprietary authentication systems. In the enterprise environment with its hybrid mix of on-premises, cloud, and WFH digital assets and devices, this means less headache for IT when securing remote access.
This way, IT can quickly adapt your document use policies to fit remote work scenarios. It also means that when your company shuts off access to an employee for good, it doesn’t run the risk anymore that a critical resource gets overlooked.
Fasoo Enterprise DRM’s encryption renders protected files useless for the former employee and other unauthorized 3rd parties.
*
Talk to our team about how Fasoo Enterprise DRM will complement and strengthen your insider risk program.
This post was originally published in March 2021 and has been updated for accuracy and comprehensiveness.