Do you know where all your sensitive PDF files are stored? How well are they protected, and who can access them?
Do you know where all your sensitive PDF files are stored? How well are they protected, and who can access them?
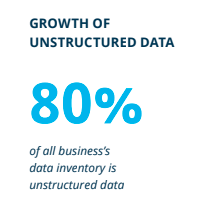
Answering these questions becomes more urgent as unstructured data now accounts for about 80% of business data inventories. Adobe’s platform-independent PDF files make up a large share of that.
So how can you protect PDF files from prying eyes and against unauthorized editing, printing, copying, or screenshots? You have several options to pick from:
At-a-glance overview: 6 methods to protect PDF files
1. PDF password protection
At the most basic level, you can protect PDF files with a password. This feature encrypts the file and also allows you to lock in print, edit, and copy restrictions for the file.
Upside: Adobe Acrobat, 3rd-party PDF editors, downloadable tools, and specialized web apps all enable you to password-protect a PDF file.
Downside: It’s better than nothing, but that’s about it. Experts agree that passwords provide a false sense of security and poor protection at best. Tools to “recover” (= crack), circumvent, or remove PDF passwords are readily available. Sometimes, simple guesswork may be faster: 20% of passwords in Fortune 500 companies were the company name or a variation, security researchers for VPN provider NordPass reported in June 2021.
Screenshot: PDF password removal tools
2. PDF encryption
The shortcomings of individual password-based PDF encryption make it insufficient for serious document protection. What happens when a big law firm needs to circulate a “strictly confidential” PDF document among the partners or a manufacturing company shares a PDF of its latest design with its supply chain, for example? This scenario requires a far more robust approach. Enter Digital Rights Management (DRM).
Fasoo Enterprise DRM, as an example, integrates with the organization’s centralized user access and policy controls. When a PDF (or any document) is created, it gets automatically encrypted – no manual password-setting required. The policy server passes the user credentials to an authentication service, such as Microsoft Active Directory (AD) or SAML, to validate and authenticate users and their document permissions.
Upside: Password-based encryption doesn’t prevent people from picking weak passwords or sharing them with unauthorized users. DRM with access control integration and centralized policy management solves this problem and allows you to change document access and permissions after the PDF is distributed.
Downside: Encryption standards, tools, and cloud services for PDF encryption vary. Many DRM solutions cover only a limited range of use cases or document formats. Others, such as Microsoft’s Azure Information Protection (AIP), require specific training and hands-on intervention from PDF users and IT admins.
3. On-screen PDF protection
Did you consider the risk posed by the Print Screen key, screen capture programs, or smartphone cameras? Specialized solutions that protect a sensitive document while in use enable you to block or discourage efforts by insiders with access to the PDF to capture its content as an image.
Upside: The standard copy and editing restrictions on password-protected PDFs are too easily circumvented. On-screen PDF protection, such as Fasoo Smart Screen, enables IT administrators to block and monitor screen capture attempts.
Downside: It’s impossible to prevent a determined person from taking PDF snapshots with a smartphone or camera, no matter what. That’s why effective deterrence is essential. For instance, with Fasoo Smart Screen, admins can put a visible “smart” watermark on sensitive PDFs. It contains user-specific information, such as the screen location and who is using it.
4. PDF sanitization
PDF sanitization removes sensitive metadata and other elements, such as comments, JavaScript Actions, or hidden layers, from the document.
Upside: Sanitizing PDFs prevents the inadvertent and potentially harmful leakage of data when a PDF is shared or published. Metadata and other information buried deep in PDFs can be used to identify employees running outdated software, making them more susceptible to spyware attacks. It also allows outsiders to gather intelligence about an organization’s internal structures.
Example: A personal assistant’s name gleaned from a non-sanitized PDF allows an attacker to pose as that person in a phishing email sent to a corporation’s CFO.
Security researchers from the University of Grenoble (France) analyzed PDF metadata of 75 security agencies from 47 countries. “We identified only 7 security agencies which sanitize few of their PDF files before publishing,” they reported earlier this year. The team still found sensitive information within 65% of sanitized PDF files, attributed to “weak sanitization techniques”.
Downside: None for any government agency, regulated organization, or global enterprise with sensitive data and systems to protect. Tools to sanitize PDFs files are available from Adobe and companies that have specialized in document sanitation software.
5. PDF usage logs
Keeping tabs on PDFs goes a long way towards effective document protection. Enterprise-level DRM solutions use dedicated servers to log who views, edits, and prints documents. They can also alert admins to security breaches.
Upside: Mainly for agencies handling classified information, government contractors, regulated industries, and corporations with large intellectual property caches to protect. They cannot afford to lose track of critical PDFs. The Fasoo Integrated Log Manager (FILM), for example, enables security and compliance teams to monitor each document’s usage throughout its lifecycle.
Downside: Businesses that use niche DRM tools report performance issues and productivity loss at scale because employees have to be online when opening PDFs tracked by a 3rd-party server. Fasoo’s mature Enterprise DRM technology, on the other hand, has rendered this effect a non-issue, even for global corporations with hundreds of thousands of employees. PDF usage is tracked online and offline.
6. PDF-on-a-stick
Use a dedicated USB thumb drive with hardware encryption as your portable PDF vault.
Upside: This method makes the most sense for PDF files intended for a small circle of one-at-a-time viewers or editors. USB sticks with a built-in fingerprint reader work best for this purpose.
Downside: Keep in mind that thumb drives are not designed for long-term data storage of more than 10 years. USB sticks also get lost, stolen, or mixed up. Thumb drives protected merely with a numeric passcode or password are still susceptible to hacking or guessing (see: PDF password protection).
And the best PDF protection is…
Of the methods presented here, which offers the strongest PDF protection? Any of them has its advantages and disadvantages. The answer depends primarily on the specific situation and data that needs to be protected.
What they have in common: None of these measures can, by itself, provide effective and efficient PDF document protection. That would require combining and hardening them.
Key in this context is the number of PDF versions and file formats you need to cover. What PDF iterations can the software under review actually protect? Fasoo Enterprise DRM, for example, supports more than 200 file formats. It adds an extra layer of protection to each document at the point of creation.
Centralized policy management, flexible exception handling, and granular permission control ensure that PDFs – and other unstructured data – are protected at rest, in use, and in transit.
PDF protection for (file) life
This data-centric and platform-agnostic file protection is controlled via Fasoo servers. It applies whenever, wherever a PDF file is accessed from any device, inside or outside the organization, online or offline.
And yes, it would also have your back when USB thumb drives are involved. With summer vacation upon us, does that mean you need enterprise-level DRM for your passport and airline tickets?
Only if you’re also reviewing corporate financial data or sales plans on the beach. Otherwise, you should be fine. That fingerprint-protected PDF-on-a-stick will do.
###
PDF files often contain sensitive information. Find out more about data that requires extra protection in this brief:
What Unstructured Data is Sensitive?