One such standard is the Data Security Maturity Model (DSMM), which provides a framework for organizations to assess their data security capabilities and develop a roadmap for improvement. The DSMM has five levels of maturity, each of which represents a higher level of data security capability. The Comprehensive Cyber Capabilities Working Group (C3WG) just released v2.0 of the DSSM.
Key Functions of the Data Security Maturity Model
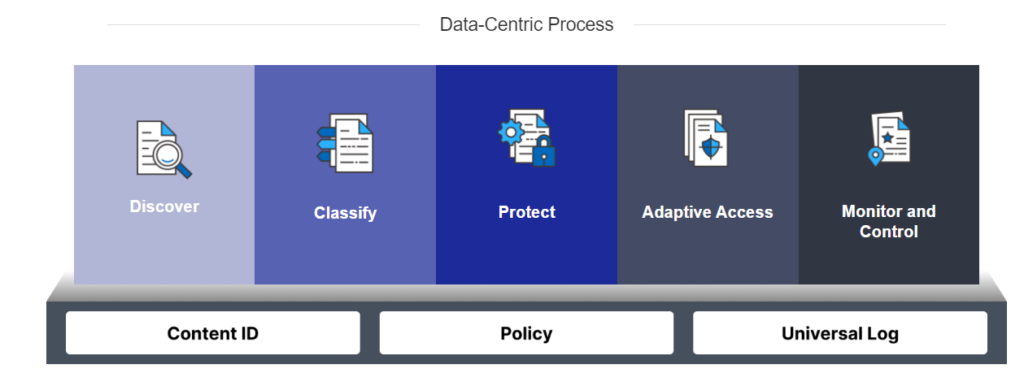
Many security models cover key aspects of data security and privacy, but the DSMM brings a uniquely data-centric approach not found in other models. Traditional data protection strategies typically focus on narrowly defined use cases or specific threats. The DSMM takes a broad, more consistent approach to protect all data. Such an approach is a growing priority as enterprise data has become incredibly dynamic in how people use it and where it resides. Users constantly access, modify and share data in numerous applications and devices. Data can exist virtually anywhere, including in end-user devices, traditional and SaaS applications, file servers, and a variety of cloud services.
The DSMM aligns with the structure of the NIST Cybersecurity Framework, providing a 1 – 3 level of maturity across the 5 functions of a data security program.
A data-centric approach to security ensures that you can apply risk context and policy enforcement to any data and can follow the data itself wherever it moves or however, it is modified. Instead of relying on network-based boundaries, a data-centric approach is able to follow the data without losing visibility and control. This approach is essential for organizations to fully leverage the power of their data while also keeping it safe from external threats, insider threats, or simple mistakes that can put the availability, confidentiality, or integrity of data at risk.
Identify and Classify
An organization must continuously discover data, classify it, and understand the risk associated with the storage, processing, or transfer of data. More specifically, risks include:
- Data availability: information being lost or not available
- Data integrity: malicious and intended or accidental altering of data
- Data confidentiality: data being exposed to unauthorized entities
Higher levels of maturity will force organizations to expand their efforts beyond narrowly defined projects or regulatory requirements. This often requires a more open-ended approach to assess data security and include additional types of data or use cases in the data security program. The open-ended approach provides meaningful security and business outcomes by addressing the root causes of an organization’s risk. This may lead to a reduction in security events and less work for security teams, who can then shift from reactive efforts to a more proactive approach.
The Fasoo Data Security Platform provides a proactive approach to data security by classifying sensitive data and applying security policies to it. You can discover where your sensitive data is located and who has access to it. This visibility can help you better understand data security risks and take steps to mitigate them.
Fasoo discovers sensitive data in databases and files on servers, in the cloud, or endpoint devices using patterns, keywords, context, file types, or attributes in pre-defined or custom detection rule templates. Enforcement rules can immediately classify and add a label to files, quarantine, or assign adaptive access control to authorized users.
A key component of assessing your data is to reduce the risk of unwanted exposure, by proactively eliminating data that you no longer need or is obsolete. Fasoo’s data categorization allows you to understand current data (less than a year old), obsolete and redundant data. Many regulations, like HIPAA or PCI-DSS, require you to retain records for defined periods of time. Data retention must balance the need to ensure unnecessary data is not retained while preventing other types of data from being inadvertently deleted. Managing redundant and obsolete data also reduces productivity, since users may not know what is current and use the wrong information.
Protect
Once you identify sensitive data, you should implement policies to proactively minimize its exposure, in particular by controlling how it is accessed, used, and retained. This is critical as it covers the policies and procedures aimed at preventing data-related security events.
While identifying and classifying data helps map out your data risk, protecting it focuses on mitigating that risk. Most organizations have multiple types of sensitive data, and the appropriate level of protection can vary based on the type of data or business use case. A single piece of content may contain multiple types or classifications of sensitive data (e.g., PII and PHI), and you may need to consider which protection rules should take precedence when protecting data.
Fasoo provides a proactive approach to data security by applying encryption, explicit access control, and tracking files and documents identified as sensitive. By encrypting files and adding granular controls, you can limit editing, printing, and sharing of sensitive content with unauthorized users inside and outside your organization. Additional measures to prevent screen captures or add watermarks to sensitive data limits other often overlooked exfiltration vectors. This prevents accidental or intentional misuse or undesired movement of data by those users with a legitimate need to use it. It also ensures that attackers cannot use the data even if stolen.
You also need to balance policy enforcement and user productivity. This may require allowing users to override a policy to get their work done. Increasing levels of DSSM maturity are characterized by progressively broader options for enabling user inputs, such as policy change requests, based on business needs and adjusting policies accordingly. Fasoo enforces data handling policies with minimum impact on usability and productivity, including the ability to request an exception to current policy. A user may need to request additional permissions to a file or may need to opt out of applying a watermark to a printed document. They can do this through a simple exception management workflow that allows data owners, department heads, or others to approve these changes for a specific file.
Another element of usability is to minimize changes to existing workflows. With Fasoo users open documents in their native applications and work with them as they do with plain documents. Policies govern in-use actions regardless of where the document is stored or who has access to it. This data-centric approach ensures that the data is protected at all times even after it leaves approved locations or goes outside the organization.
Detect
The collection and analysis of data to identify data-related security events or policy violations uncover risks or violations not stopped by your protection measures. Detection is not a reactive process, but one that helps detect risks and threats as early as possible to minimize any impact.
The discovery of risky or anomalous behaviors, such as unusual data downloads, excessive printing, or accessing unauthorized copies of sensitive data, may pose a threat to your organization. Since tracking the movement of data can be challenging, it is better to monitor and manage the usage of sensitive data. Fasoo collects user access logs into a single console making it easier to correlate actions to help identify potential data breaches and policy violations.
If users remove security protections on files, Fasoo can enforce them again in real time. Scanning policies detect sensitive data as users create, move or save documents, and apply the appropriate security policy to the document. This provides proactive security and enforces policies before any malicious or unintended sharing of sensitive data occurs.
Respond
If there is a data security incident, you should immediately minimize the threat. Objectives include validating and establishing the scope of the incident, taking steps to minimize the impact, and maintaining communication with business stakeholders and other affected parties.
Many organizations already have solid processes and procedures to respond to cybersecurity incidents. You may need to adjust them to increase the focus on data since many responses focus on the network, devices, or other locations.
With Fasoo, you can monitor access to your sensitive data in real time and receive alerts when you detect suspicious activity. By encrypting and controlling real-time access to sensitive files and documents, alerts decrease since you don’t have to monitor locations and devices. Only authorized users can access the sensitive data and you can adjust policies quickly if needed. This allows you to respond quickly to security incidents and minimize their impact.
Recover and Improve
You may need to recover from a security incident by restoring normal operations. Even if no events occur, you need to evolve your overall data security program regularly. This involves identifying and incorporating lessons learned into your program. This indicates you are proactive in your approach to data security and are always looking for ways to improve.
Fasoo helps you understand your data usage and how to optimize your security policies to minimize the risk to your data. Since users can request policy exceptions to meet specific use cases, you may need to adjust their policies to reduce the workload of approvers. If users change roles in your organization, you can also change policies to meet their new roles. By centrally controlling data security policies, you can automatically apply them as users move into different departments or as the sensitivity of data changes.
Conclusion
The Fasoo Data Security Platform is a powerful data security tool that can help you at every level of the Data Security Maturity Model. Whether you are just starting to develop a data security program or have a fully optimized program in place, Fasoo can minimize your risk to sensitive data while having minimal impact on user productivity.
Read more about how the Fasoo Data Security Platform can help you meet the DSSM.