Email is still the medium we use the most to communicate information to friends, coworkers, customers and business partners. It’s available on any platform and it becomes a default filing cabinet for many of us. Because of its ubiquity, a person with malicious intent can cause a lot of havoc by simply emailing sensitive information to themselves or a confederate.
Here are two interesting examples of sending information to the wrong person. One was accidental and the other deliberate.
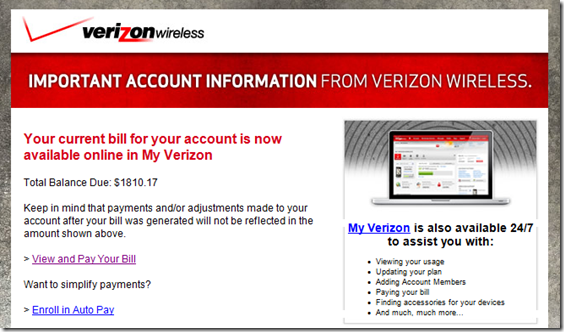
I use Verizon Wireless as my cellphone carrier. I get an email from them every month reminding me to pay my bill. In the email is my total balance due and a link to click if I want to pay it online. It’s very convenient and I appreciate the service. The email also contains the last 9 digits of my account number. Imagine my surprise when I got an email from Verizon saying my monthly bill was $1810!
By examining the email shown below, I noticed there was no account number and there were 9 other recipients in the To: line. At first I thought it was spam, but everything else looked legitimate, including the sender address. I concluded that this was a mistake and the total balance due was the sum of all the customer’s bills. I got my legitimate reminder later in the day. Fortunately no account information was shown, but now I have the email addresses of 9 other Verizon Wireless customers. This could be a perfect opportunity for a phishing scam.
A deliberate act of stealing information also occurred this week using email. An employee from the South Carolina Department of Health and Human Services compiled medical information from about 228,000 people and sent it to his private email account. He gathered this information into a spreadsheet over the last few months. It contained Medicaid ID numbers, which are linked to Social Security numbers. Other people had their names, addresses, phone numbers and birth dates stolen.
The agency estimates it will cost about $1 million to hire a firm that is contacting the affected patients and offering personal information protection. A security review and upgrade will cost up to $500,000. The state could also face federal penalties for violating patient confidentiality laws with a maximum fine of $1.5 million. This data breach could cost the state of South Carolina at least $3 million. There are probably other costs that they haven’t yet thought of, so the true cost will be much higher.
In both cases, emails were sent to unauthorized people. Imagine if Verizon and the South Carolina DHHS had a way to “kill” the attachments after they had been sent. Persistent file-level security allows organizations to manage sensitive information after it has left the premises – either intentionally or unintentionally. They could define a policy so that any document with specific information, like an account number or Medicaid ID, is encrypted and the document limited to certain people. The policy can control who can open the file, what editing features are available, the time frame within which the file can be opened and the ability to revoke all access rights if the file was sent out in error. That turns an oops into a non-event.
Inadvertently sending documents to the wrong person can be embarrassing or cause major financial and legal problems. Malicious theft is even worse. Look at simple tools to prevent these problems in the first place. We all would love an undo switch and persistent document security gives you that.
Photo credit The Atlantic Wire