As data is moving and multiplying at a rapid pace across boundaries, platforms and applications, users have the ability to access data in a variety of ways and data very rarely stays within the secure perimeter of an enterprise anymore.
With more and more sensitive data residing outside of the corporate perimeter, locating, securing and controlling this data presents a significant challenge. The traditional security strategies that businesses have been relying on are no longer the viable option they once were.
Businesses need to understand the risks to their data, keeping up to date with the constantly evolving threat landscape. You shouldn’t be protecting the crown jewels of your business using only perimeter security technologies, since it’s obvious that they are no match for today’s criminals.
In our current perimeter-less world, many CISOs realize that data centric security is the best method to secure sensitive data. They realize that data is vulnerable to security breaches and theft and that encryption should go down to the document level to ensure that any document is safe where it is stored, while it is in transit, and when it is being viewed by any authorized users. Security is now becoming part of every stage of a document’s lifecycle — from creation to transmission, storage, editing and retrieval.
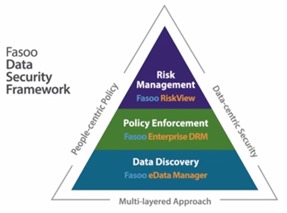
Three building blocks are key to building a data-centric security framework:
1. Data Discovery – The ability to implement a data security and governance strategy begins by identifying sensitive data at the source, wherever that may be. Security has to travel with the data, no matter where the data goes. By identifying and analyzing sensitive data, enterprises can focus on managing and securing it. Data discovery allows you to understand relationships between users and data that is created. It helps you see how information multiplies and proliferates within the perimeter and how it’s used by different groups, line of business and mobile applications.
2. Policy-based encryption and usage governance – This enables you to secure and define the types of data an authorized user can access based on their roles. Organizations need a baseline level of security that meets the overall company policy, but also higher security levels and controls for specific business units or users that need it. A customer service representative may only need to see a customer’s order history, but not financial information. Limiting what data authorized users can access and what actions they can take on this can greatly reduce the ability for a current or former employee to expose or steal sensitive data. This approach can further demonstrate that an enterprise is enforcing security and privacy regulatory policies.
3. Risk Management – It is essential to visualize and manage risks by correlating logs of authorized data usage with other user activity. Having a comprehensive view of how sensitive data exits a perimeter or as sensitive data appears where it is not supposed to be, can provide business managers a level of intervention for risk management.
Clearly data is imperative to conduct business today and this brings the need for security and protection of sensitive data; all the time, anywhere. A data-centric security framework does this and even goes further to provide enterprises with the ability to revoke all access to data as needed.

