Remote Work
Secure Workflows Wherever You Go
Secure Remote Work Environment
As remote work becomes the norm, sensitive data is more vulnerable than ever. Traditional endpoint protection is no longer enough. How can you secure your data in a distributed work environment? The answer is simple…
71% of security leaders lack full visibility into remote employee home networks.
Source: Tenable
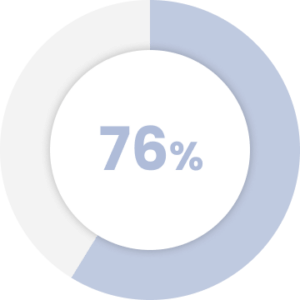
of office workers say working from home during COVID-19 has blurred the lines between their personal and professional lives.
Source: Securitymagazine.com
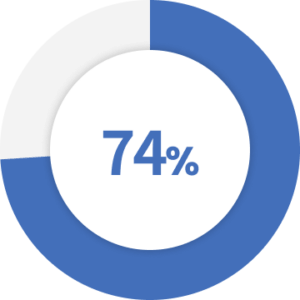
of organizations attribute recent business-impacting cyberattacks to remote work tech vulnerabilities.
Source: Tenable
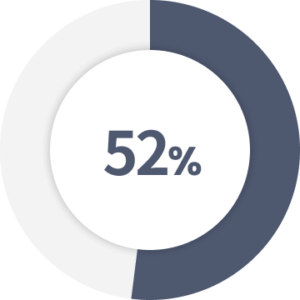
of legal and compliance leaders are concerned about third-party cyber risks due to remote work.
Source: Gartner
The global transformation to remote work exposes sensitive documents to greater risks, making comprehensive data security solutions essential to protect your organization's valuable assets.
BYOD use and storing sensitive documents
Restrict user actions on sensitive data, regardless of the device.
Document rights prevent unauthorized activities while allowing employees to remain productive on their personal devices.
Unauthorized cloud services
Apply persistent document access controls and encryption to ensure data protection.
Enterprise security policies are consistently enforced across hybrid and multi-cloud environments.
Lost visibility across multiple collaboration platforms
Embed a document ID tracker to automatically log all access and usage.
Maintain complete lifecycle visibility with a single, self-reporting log for easy audit and compliance reporting.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with a Data Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Work From Home Solution eBook
How secure is your company data in a work from home environment? Protect documents as they are shared, printed and displayed on the screen while not impacting productivity.

How Can Your Remote Workforce Collaborate Securely?

How to Ramp Up Your Remote Work Document Protection

Whitepaper: Fasoo EDRM

Financial Services: How to Boost Your Remote Work Surveillance

