Endpoint Security
Secure Every Device, Ensure Every Action

How Do You Protect Your Endpoints?
Each company endpoint serves as a gateway to corporate data. Employees may use personal devices (BYOD) to access sensitive information, potentially exposing it through unauthorized sharing methods such as printing and capturing screenshots. Traditional endpoint protection solutions often fall short in mitigating these risks.
Up to 70% of successful data breaches and 90% of cyberattacks originate from endpoint devices.
Source: IBM
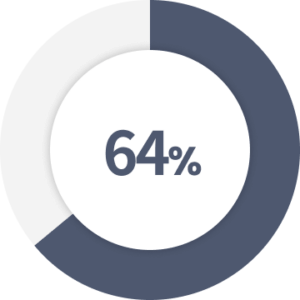
of organizations reported a print-related data loss in the last year.
Source: Quocirca
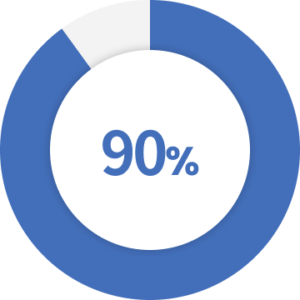
of cyberattacks rely on some form of social engineering.
Source: Security Boulevard
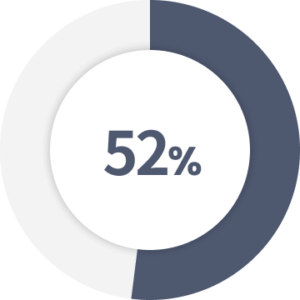
of legal and compliance leaders are concerned about third-party cyber risks due to remote work.
Source: Gartner
Unmanaged personal devices (BYOD), printing, and screens put sensitive documents at increased risk.
Using personal devices (BYOD) and storing sensitive documents
Assign explicit, granular rights to documents to control data in use.
Enforce the principle of least privileges, preventing unauthorized sharing and misuse of sensitive documents.
Printing sensitive data and sharing it with unauthorized people
Add watermarks to sensitive documents or prevent printing of sensitive data altogether.
Minimize the risks of data breaches resulting from unauthorized printouts and printing.
Capturing sensitive data on a screen and sending it to unauthorized users
Add watermarks to sensitive data on the screen or block all screen capture attempts.
Limit and deter data breaches by preventing unauthorized screen capture attempts.
Key Features


Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with an Endpoint Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Fasoo Smart Print eBook

How Fasoo Enables Zero Trust Data Security

Fasoo Smart Screen eBook

How to Ramp Up Your Remote Work Document Protection

Document Security: What Is Secure Print?

