Insider Threat
Stop Threats from Within, Secure What's Yours
Insider Threat: Always a Possibility
Highly publicized insider data thefts and security breaches highlight the growing need for enhanced security solutions to mitigate the risks posed by both malicious and unintentional insider actions.
Do you know where your organization is most vulnerable?
95% of cybersecurity breaches are caused by human error.
Source: Cybint
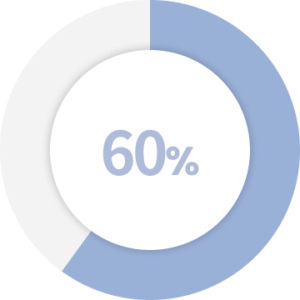
In 2020, 60% of data breaches were from insiders.
Source: Techjury.com
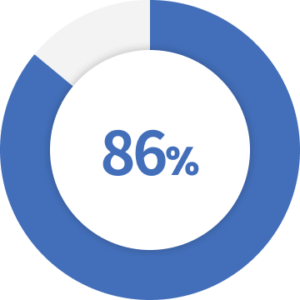
of breaches were financially motivated and 10% were motivated by espionage.
Source: Verizon
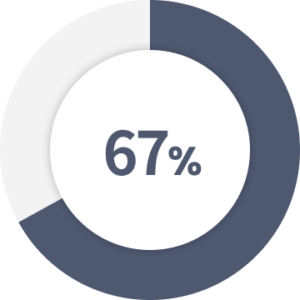
of accidental insider threats still come from phishing attacks.
Source: Techjury.com
Insider threat risks are outpacing today’s monitor and alert systems, leaving organizations exposed to potential breaches.
Insider breaches go undetected for months, leaving sensitive documents vulnerable.
Secure documents proactively with persistent encryption, preventing exposure before an incident occurs.
Even if a breach happens, encrypted documents remain inaccessible to threat actors.
Documents are vulnerable when decrypted and accessible without retrictions.
Apply granular rights policies to protect documents while in use, ensuring that only authorized actions are allowed.
High-risk insider threat behaviors are effectively controlled and restricted, reducing the potential for misuse.
Contractors and supply chain partners can pose insider threats.
Implement persistent controls and restrictions that remain in place, regardless of where the documents are accessed or shared.
Security measures are inherited and enforced across your contractors and supply chain partners, ensuring consistent protection of sensitive data.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with a Data Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Automotive Parts Manufacturer Protects IP

Webinar: Close the Gap on Insider Threat: Granular Access

10 Tips to Counter Insider Threat in the Automotive Industry

Risky Business: How Company Insiders Put High Value Information at Risk

Trade Secrets and Insider Threats – Levandowski’s Are Everywhere

