What is Advanced Data Security (ADS)?
Advanced Data Security (ADS) is a comprehensive, data-centric approach that protects sensitive information across its entire lifecycle – creation, sharing, storage, and disposal. Rather than relying on fragmented tools, ADS consolidates security functions into an integrated platform, offering a unified and consistent defense built on zero-trust principles.
By enforcing persistent and consistent security policies, ADS ensures that protections remain in place regardless of where data travels or who accesses it. This includes dynamic access controls, strong encryption, and data-aware monitoring that adapts to context and risk.
Advanced Data Security also delivers greater visibility and control through capabilities like data posture management, audit-grade logging, and continuous risk assessment. These elements empower organizations to proactively identify vulnerabilities, enhance compliance, and confidently manage sensitive data, even in complex, hybrid environments where threats evolve rapidly.
In short, ADS is not just a defensive measure – it’s a strategic foundation for resilient, compliant, and intelligent data operations.
Why Advanced Data Security Matters
In today’s landscape of cloud computing, remote work, and generative AI, sensitive data is no longer confined to corporate firewalls. It is often shared across devices, platforms, and users, including third parties and external collaborators. Advanced data security helps:
- Protect sensitive and regulated data across endpoints, cloud, and collaboration platforms
- Maintain data visibility and control regardless of location or format
- Prevent data leaks and insider threats with granular access controls
- Support regulatory compliance (e.g., GDPR, HIPAA, PCI DSS)
- Defense against AI-driven threats, including prompt injection and model inversion
Core Capabilities of Advanced Data Security
- Data Discovery & Classification: Identify and label sensitive files (PII, IP, financial data)
- File-level Encryption: Protect data wherever it moves (email, USB, cloud)
- Granular Access Control: Apply role-, attribute-, or content-based access rights
- Persistent Controls: Enforce persistent policy controls even after sharing
- Comprehensive Audit Log: Gain insights into how data is used at all times
Fasoo Data Security Platform
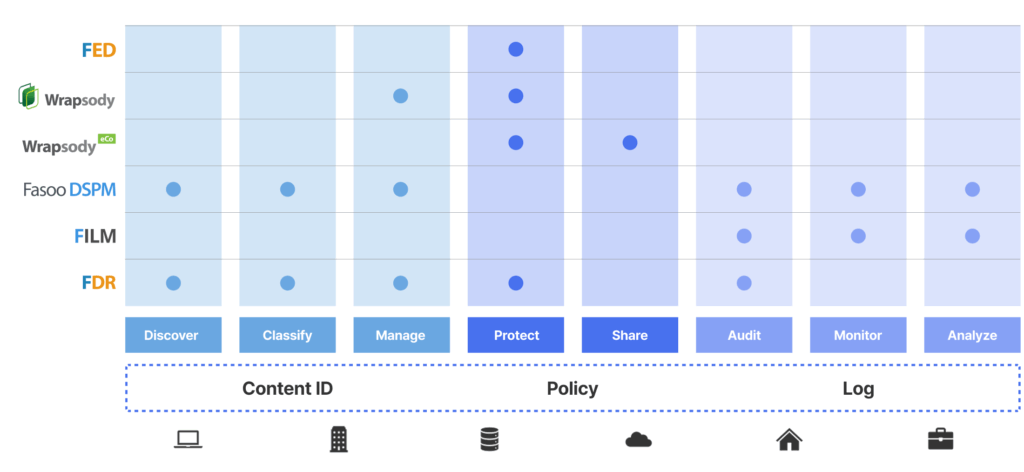
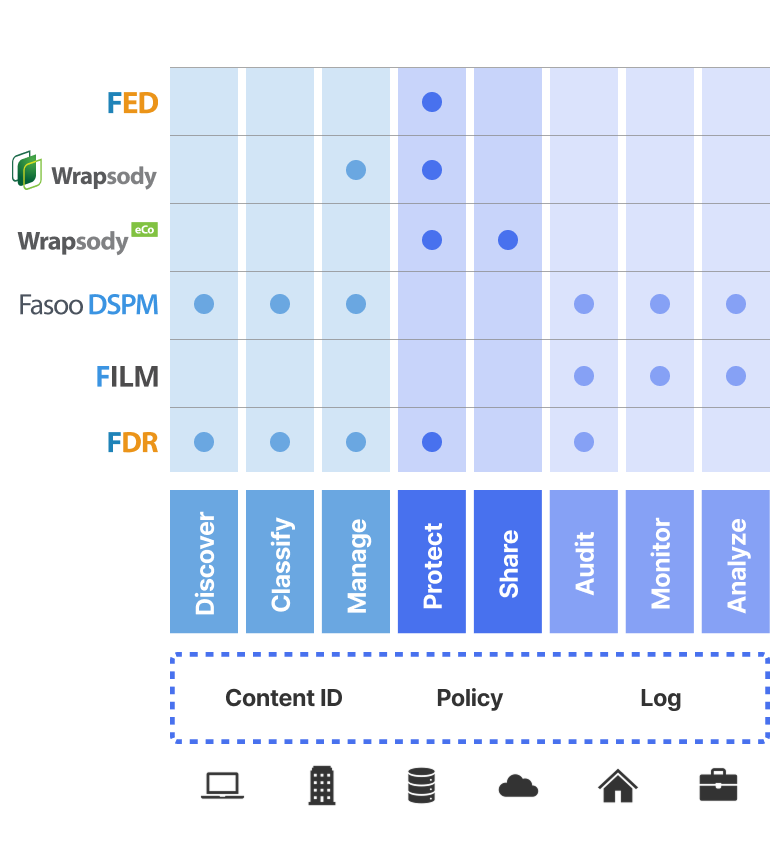
The Fasoo Data Security Platform combines the most advanced data security and management technologies to safeguard sensitive data throughout its lifecycle, regardless of location. Critical sensitive data security and privacy functions are consolidated into a single highly automated sequence of processes.
Solution | Key Features |
|---|---|
Fasoo Data Radar | • Automatically scan and identify sensitive unstructured data across endpoints, servers, and cloud repositories
• Classify data based on content, context, and usage patterns
• Apply appropriate security policies dynamically, including encryption, quarantine, and deletion
|
Fasoo Enterprise DRM | • Encrypt files at the point of creation, ensuring security travels with the data
• Control access based on user roles, devices, and other contextual factors
• Restrict actions such as viewing, editing, printing, and sharing based on predefined policies
|
Fasoo DSPM | • Provide real-time insights into data access patterns and potential security vulnerabilities
• Enable organizations to assess the effectiveness of their security controls
• Facilitate compliance with regulations like GDPR, CCPA, and HIPAA by ensuring data handling aligns with policy requirements |
Wrapsody | • Eliminate version chaos through content virtualization, treating duplicate files as a single source, no matter where they are created or edited
• Track document usage in real time, including access, edit, and share, providing full visibility into how critical documents are used
• Apply content-specific access control to each virtualized file, ensuring robust security no matter where the file is stored or accessed |
Wrapsody eCo | • Securely share sensitive files with external partners without losing control
• Apply time-bound access to sent files and revoke permissions remotely
• Monitor all shared document through comprehensive audit trails, providing transparency and accountability |
Resources
Blog

Solution

Video
Fasoo Enterprise DRM
Meet with a Advanced Data Security Specialist

Solution
Explore more about
Advanced Data Security

