Generative AI and cloud computing are rapidly transforming the way businesses operate. From automating tasks to streamlining global collaboration, these technologies are driving innovation at an unprecedented pace. But while the benefits are clear, they come with equally significant security challenges. Organizations now deal with environments where sensitive information is constantly in motion – shared across devices, regions, and platforms they no longer fully control.
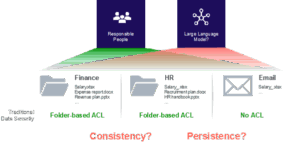
In this new digital paradigm, data is no longer confined within the perimeter of the corporate network. Employees are feeding sensitive inputs into AI tools, files are moving fluidly between cloud services, and access is being granted across borders and time zones. This decentralization makes traditional, infrastructure-centric security models increasingly ineffective. To stay ahead of evolving threats, businesses must adopt a more advanced and holistic approach to protecting their data – prioritizing control, visibility, and adaptability.
Fig. 1 – Traditional data security, not assuring consistency and persistence of security polices in the AI era
The GenAI Dilemma: Productivity vs Privacy
Generative AI platforms like ChatGPT, Gemini, and Copilot are powerful, but they also introduce significant risks around data exposure. These tools are designed to generate content based on user inputs, but those inputs often include sensitive or proprietary information. The lack of visibility and control over how these tools store or process data makes it difficult to ensure compliance with internal policies or external regulations.
Here are some of the most pressing risks:
- Unintentional disclosure: Users may input sensitive data, such as customer information, strategic plans, or source code, into prompts without realizing the long-term implications.
- Opaque data handling: Many AI platforms do not clearly explain how input data is stored, used, or retained, raising questions about whether it could be used to train future models.
- Unpredictable response: AI-generated content might inadvertently reflect confidential data patterns or create outputs that reveal protected information.
- Post-generation exposure: Once content is generated, it can easily be printed, copied, or shared without restriction, making containment nearly impossible.
These risks demonstrate how GenAI bypasses traditional data governance models. Security teams may never even know that sensitive data has been exposed. This highlights the urgent need for persistent data protection policies that are integrated directly into workflows and tools, securing not only data at rest but also its usage and output.
Cloud Environments: Flexibility with a Trade-Off
The cloud enables agility, scalability, and cost savings, but it also fragments data across multiple systems and geographies. Cloud platforms, by nature, abstract the underlying infrastructure from the user. This abstraction creates a trade-off: organizations benefit from speed and scalability, but they also lose the ability to enforce consistent, end-to-end control.
Key challenges include:
- Loss of direct control: Once data is moved to the cloud, it’s subject to the provider’s policies and infrastructure. Businesses often don’t have full visibility into where their data resides.
- Compliance complexity: Regulations like GDPR, HIPAA, and regional sovereignty laws require strict data governance. Multi-cloud and hybrid environments make consistent compliance monitoring more difficult.
- Shadow IT and data sprawl: Employees may use unsanctioned cloud services to store or share data, creating unmanaged repositories of sensitive information.
- Identity and access sprawl: Users access corporate data from various devices and networks. Managing secure authentication across these diverse endpoints adds complexity and risk.
Together with GenAI, cloud environments contribute to a perfect storm: data is more powerful – and more vulnerable – than ever. The common thread across both trends is the loss of centralized control. Traditional parameter defenses, or even encryption alone cannot address how dynamically data is being used and shared.
Advanced Data Security: Toward a Data Security Platform
To respond to these challenges, organizations must move beyond reactive, fragmented security practices and adopt a data security platform strategy for the advanced data security. This approach is built on the principle where the focus shifts from where the data is to how its’ used, by whom, and under what conditions.
While encryption remains a necessary foundation, it’s no longer sufficient on its own. It can protect data at rest or in transit – but it doesn’t control what happens once a legitimate user decrypts and accesses that data. This is where modern threats, such as insider threats or accidental exposure through collaboration tools, slip through the cracks.
What’s needed is a shift from fragmented tools to an integrated data security platform strategy – one that focuses on providing comprehensive security to how data is accessed, processed, and shared.
Advanced Data Security (ADS) consolidates fragmented tools into an integrated platform that provides holistic data security, adopting zero-trust principles. It also:
- Applies persistent protection and policy controls to files and sensitive content, even after downloading or sharing
- Utilizes posture management to continuously assess data risk based on context
- Leverages granular access control tied to identity, device, and behaviour
- Offers visibility and audit trails to support compliance and governance needs.
Fasoo’s approach to Advanced Data Security
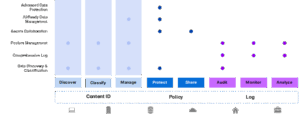
Fasoo helps organizations achieve comprehensive data security with multi-layered interrelated solutions. Fasoo’s platform unifies key capabilities – discovery, classification, protection, monitoring, and governance – into a centralized framework that scales across the enterprise.
This means that whether data is being shared through email, stored in a cloud repository, accessed via an endpoint, or entered in an AI prompt, the same consistent security policies follow. Persistent file-level encryption, dynamic watermark, and rights management ensure that control isn’t lost once the data leaves a trusted boundary.
By securing information at the data level and embedding policy enforcement into everyday workflows, Fasoo’s data security platform guarantees both consistency and persistence. Sensitive files remain protected no matter how they’re used or where they’re sent – enabling safe, compliant operations in today’s AI and cloud first environment.
Fig. 2 – Fasoo Advanced Data Security Platform
Conclusion: From a Point Solution to a Data Security Platform Strategy
As AI and cloud technologies become more deeply embedded in business operations, the surface area for data risk continues to grow. Companies can no longer afford to rely solely on infrastructure-based defenses or isolated point solutions. Instead, they must adopt a data security platform strategy – one that ensures data is discovered, governed, and protected across its entire lifecycle.
Advanced data security isn’t just about preventing breaches; it’s about enabling safe innovation. By investing in a platform-driven strategy, organizations can embrace the future of AI and cloud without compromising trust, privacy, or control.
Click to Explore more to learn how Fasoo Data Security Platform fulfils organizations’ security concerns in the modern era of AI and cloud.