IP Protection
Safeguard Innovation and Maintain Your Competitive Edge
Protect Intellectual Property (IP)
Companies are facing growing threats to their intellectual property (IP) as cyber-attacks, insider threats, and weak supply chain security expose sensitive assets.
Can your organization prevent the loss or theft of trade secrets and other valuable IP?
Recent numbers cited by government officials place American IP theft at between $225 and $600 billion annually.
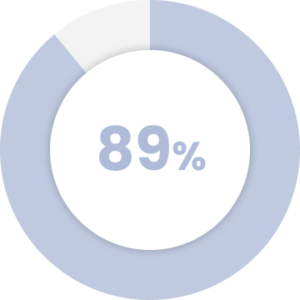
of CISOs believe a fast-paced collaborative culture puts the company at greater risk.
Source: Code42 Data Exposure Report 2019
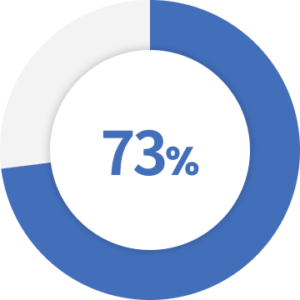
of data breaches take months or years to discover.
Source: Verizon 2019 Insider Threat Report
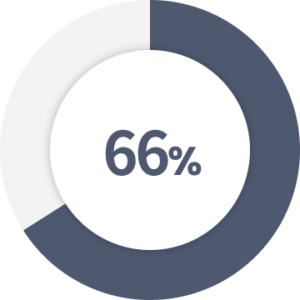
of security professionals identify significant weaknesses with solutions such as DLP, UEBA, and UAM.
Traditional office suite and data loss prevention (DLP) tools often leave enterprise IP vulnerable, especially when dealing with complex file formats.
IP formats like CAD, engineering drawings, and PDFs are not protected, or require alternative workflows.
Use application-independent solutions to secure all forms of IP, regardless of format.
Sensitive IP, often exposed by traditional security tools, is protected seamlessly without interrupting user workflows.
Authorized insiders decrypt documents and use them without restrictions.
Apply document rights policies to control data-in-use.
The highest-risk insider threats are effectively controlled, with actions on sensitive data restricted and monitored.
IP documents traverse the cloud, endpoints, and third parties, stripping original enterprise controls.
Bind identity-based policies directly to the document to maintain control.
Identity controls are persistently enforced and can be dynamically updated or revoked, regardless of where the document travels.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with an IP Protection Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Automotive Parts Manufacturer Protects IP

Fireside Chat: Stop Intellectual Property Theft

Challenges Manufacturing Companies Face

Whitepaper: Fasoo EDRM

Tariffs in the Automotive Industry is not their only concern

