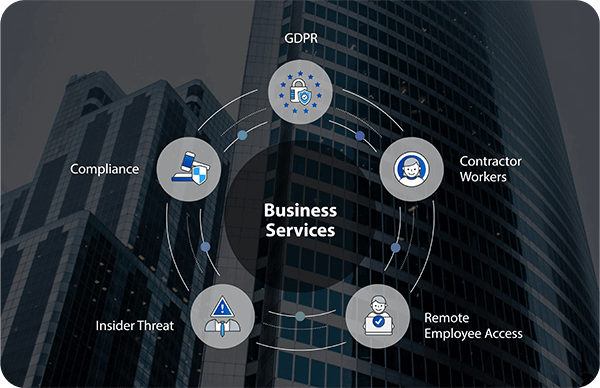
Business Services
Protect Your Clients' Data Integrity and Uphold the Trust You've Built
Protect your clients' sensitive data and intellectual property
Business services are prime targets for cybercriminals due to the sensitive data they handle. This includes critical client information such as trade secrets, personally identifiable information (PII), patentable technologies, and other intellectual property (IP). Additionally, businesses must meet stringent data protection and privacy compliance standards to maintain trust and ensure secure operations.
Solutions
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Encrypt & Remediate
Access Privileges
Trace & Audit
Our clients trust us to maintain their confidential data, and
Fasoo ensures we comply with and meet all privacy regulations.
Fasoo Enterprise DRM
Meet with a Data Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

Blog

Use Case

Blog
