Cloud Security
Secure Your Cloud, Empower Your Business
Protect Your Data Beyond Storage
Storing data in the cloud is convenient, but what happens after it’s downloaded? If the wrong person gets access, you lose control and visibility.
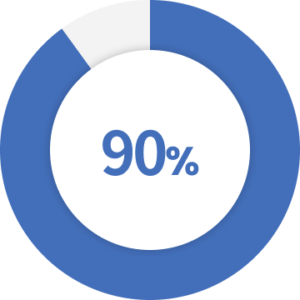
Compromise cloud accounts lead to an average financial loss of $6.2 million.
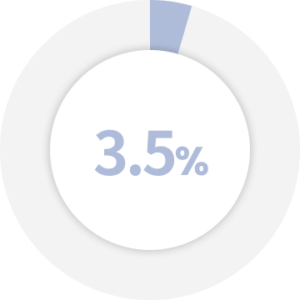
Cloud account compromises cost about 3.5% of organizational revenue in a 12-month period.
Source: cybertalk.org
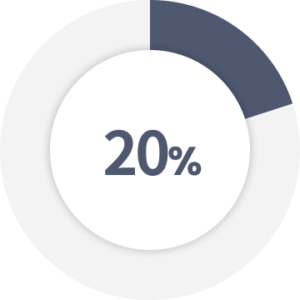
In 2020, “only” 20% of organizations experienced cloud security incidents.
Source: cybertalk.org
Organizations struggle to track and control documents across hybrid and multi-cloud environments. Without visibility, data is at risk of leaks, unauthorized access, and compliance violations.
Access to sensitive documents is often misconfigured and applied inconsistently, increasing the risk of unauthorized exposure.
Bind identity-based policies directly to the document, ensuring access is controlled at the file level.
Identity and access policies remain enforced no matter where the document travels, maintaining security and compliance.
When documents are emailed or downloaded, cloud-based security controls no longer apply, leaving data vulnerable.
Enforce enterprise security policies at the document level to ensure protection remains intact, regardless of where the file is stored or shared.
Sensitive documents retain enterprise controls at all times, preventing unauthorized access and data leaks.
Ensuring compliance with data regulations is complex, especially when documents are widely shared and modified.
Automatically classify, tag, and track sensitive documents at creation, embedding security and compliance measures from the start.
Built-in controls and tracking create an auditable document trail, simplifying compliance enforcement and regulatory reporting.
Key Features
Fasoo Data Security Platform
Fasoo fortifies and scales today’s enterprise infrastructure with strong unstructured data protection and control. Our comprehensive platform is deployed with over 2,000 customers to discover, classify, protect, control, trace, and securely share critical business information.
Discover
Classify
Protect
Adaptive Access
Monitor and Control
Fasoo Enterprise DRM
Meet with a Cloud Security Specialist

Solution
Explore more about
Fasoo Enterprise DRM

Resources

6 Vulnerable Points in Your Data Security Architecture and How You Can Protect Them
Do you know where you are most vulnerable? Now is the time to check these key trends.

Fasoo Enterprise DRM
Using a data-centric approach, Fasoo Enterprise DRM enables organizations
to protect sensitive documents persistently on any device at any time
throughout the entire document lifecycle.

The Cloud is a File Cabinet – Make Sure You Lock It
Everyone uses cloud computing. Small and mid-sized businesses see it as a great way to use services that were only available to large organizations in the past.

Are You Crazy to Store Data in the Cloud?
We love the cloud. Sharing files between your devices and colleagues is as simple as drag and drop. But without security on your files, anyone can access them.

Cloud Computing is Not Just for Big Companies
Cloud computing helps everyone become more agile and competitive. A startup can build a web presence and a large company can expand into a market with a few clicks.

Cloud Computing Explained
Some companies say that everything on the Internet is cloud computing. At it’s basic level, cloud computing is any computing capability offered on-demand over the Internet.