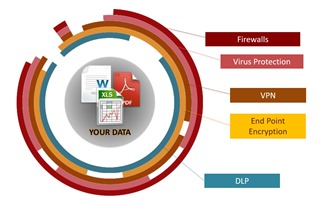
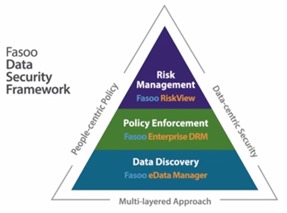
- In a recent article entitled “Securing Information for a Shared Services Infrastructure”, Richard Freeman from Ricoh Canada talked about the need to secure information as companies share it internally and externally. The focus of the article is how an organization must look at balancing the need to efficiently share information without compromising privacy, protection of intellectual property and other sensitive data, or financial and legal risk. As is evident from all the news about...
- In a recent article entitled “Securing Information for a Shared Services Infrastructure”, Richard Freeman from Ricoh Canada talked about the need to secure information...